Augmenting an Incident with GPT3
In the previous example we identified a security incident from SAP.
In this demo we will build an automation to augment the incident with more information derived from GPT3.
This demo depends on the steps we executed on the previous chapter. Don’t skip it
Setting up permissions
The SAPCAL resource group has a set of permissions that require some adjustments so we can create atuomations.
In this step we will setup those permissions correctly so Sentinel can use its resources.
-
On the Azure portal, let’s go to the Resource Groups resource page:
-
On the Resource Groups resource page, click on the resource group, select Access Control (IAM) and Add role assingment.
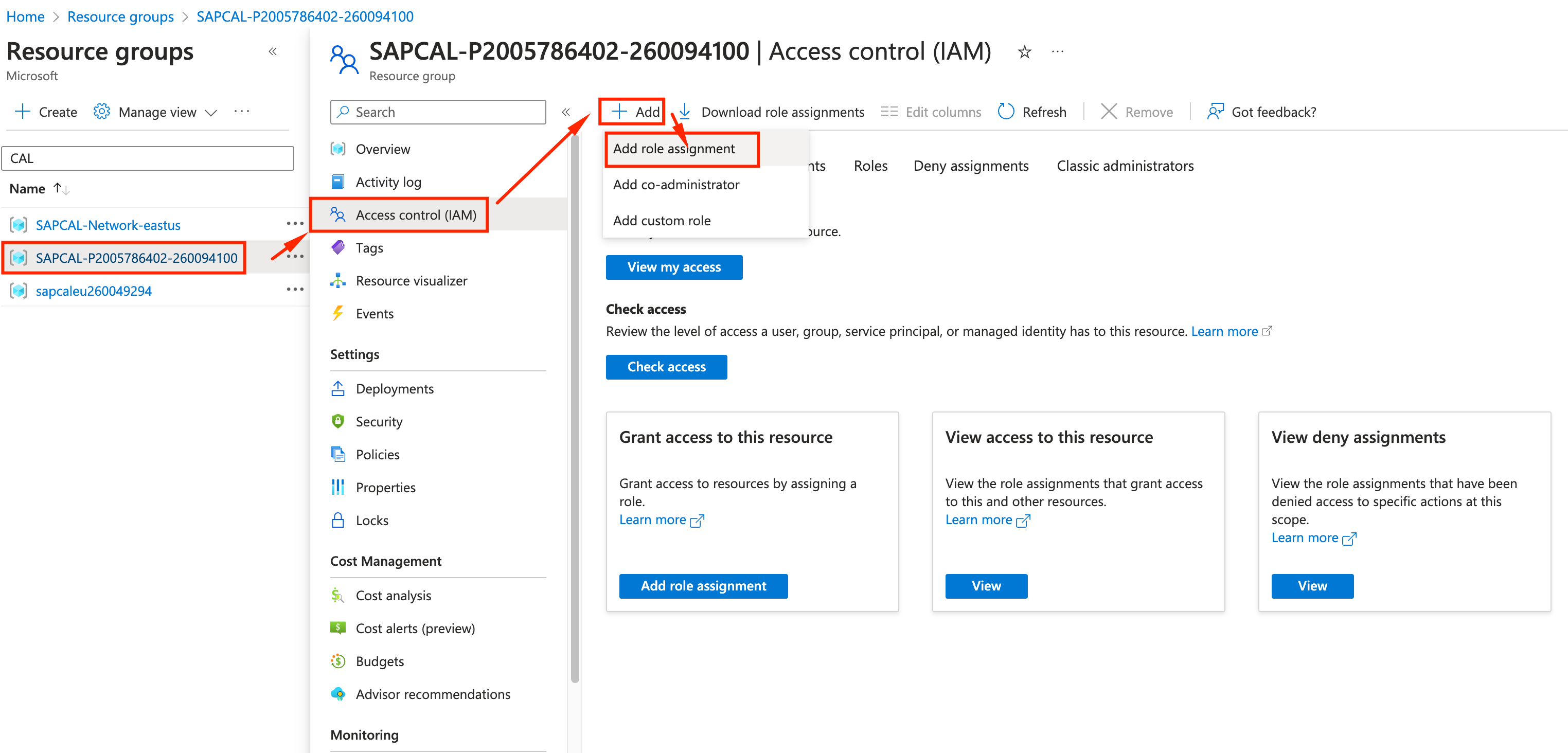
-
We will do this 2X for 2 sets of permissions: Owner and Logic App Contributor.
- Click on Owner Role and select the desired role. Click Next
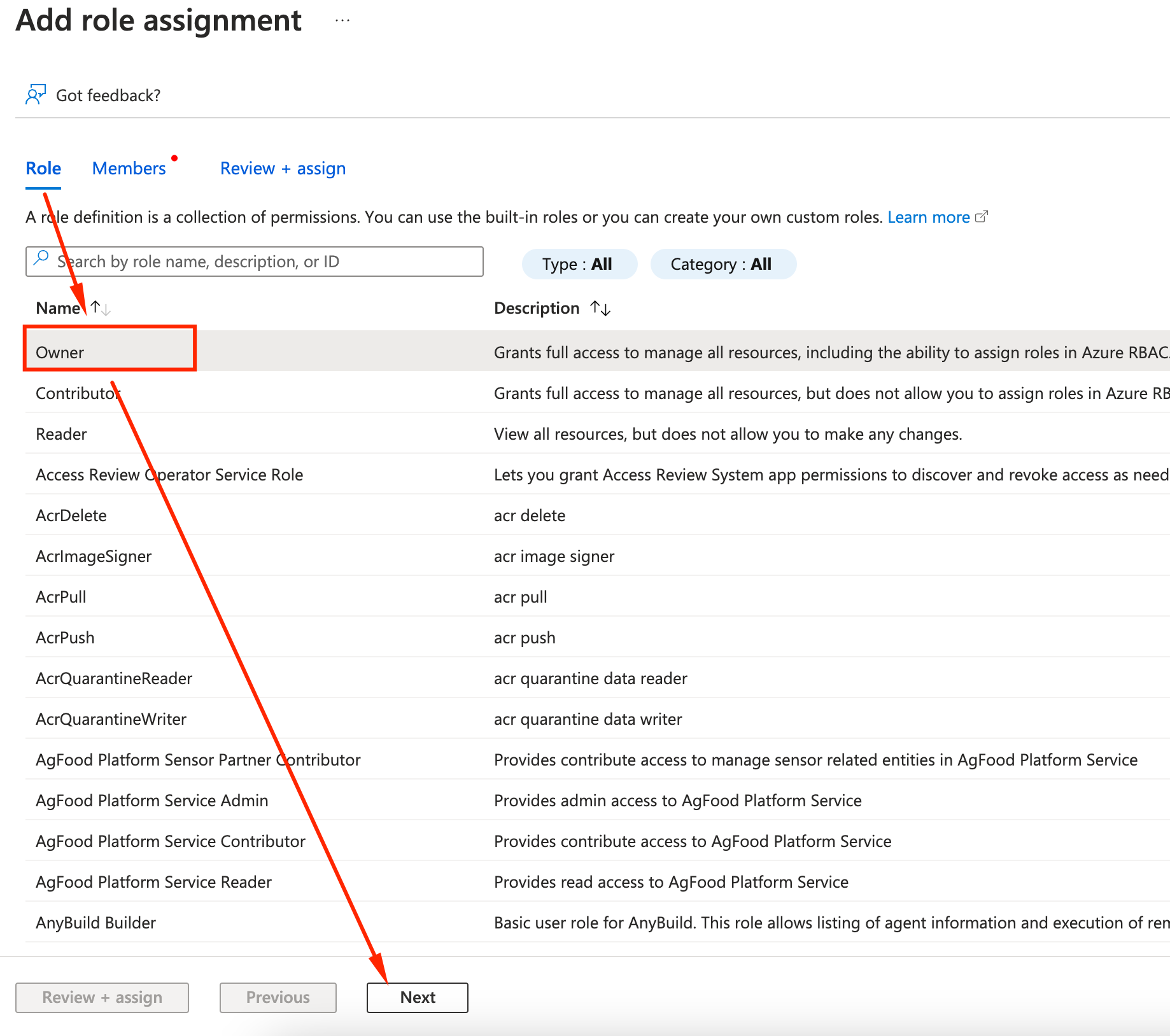
- Go to the members tab, and Select Members. Pick your user and click Select
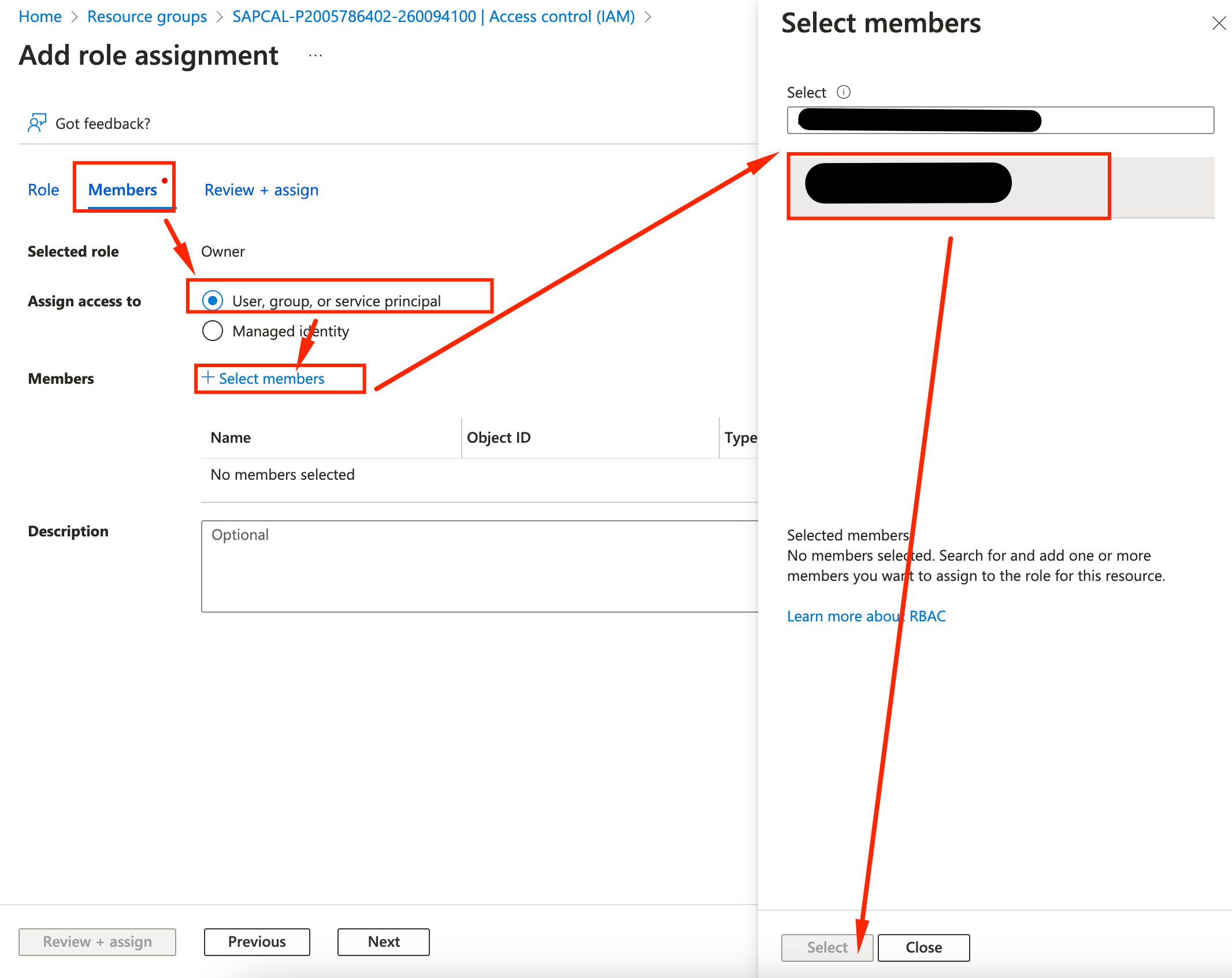
- Repeat it for the Logic App Contributor
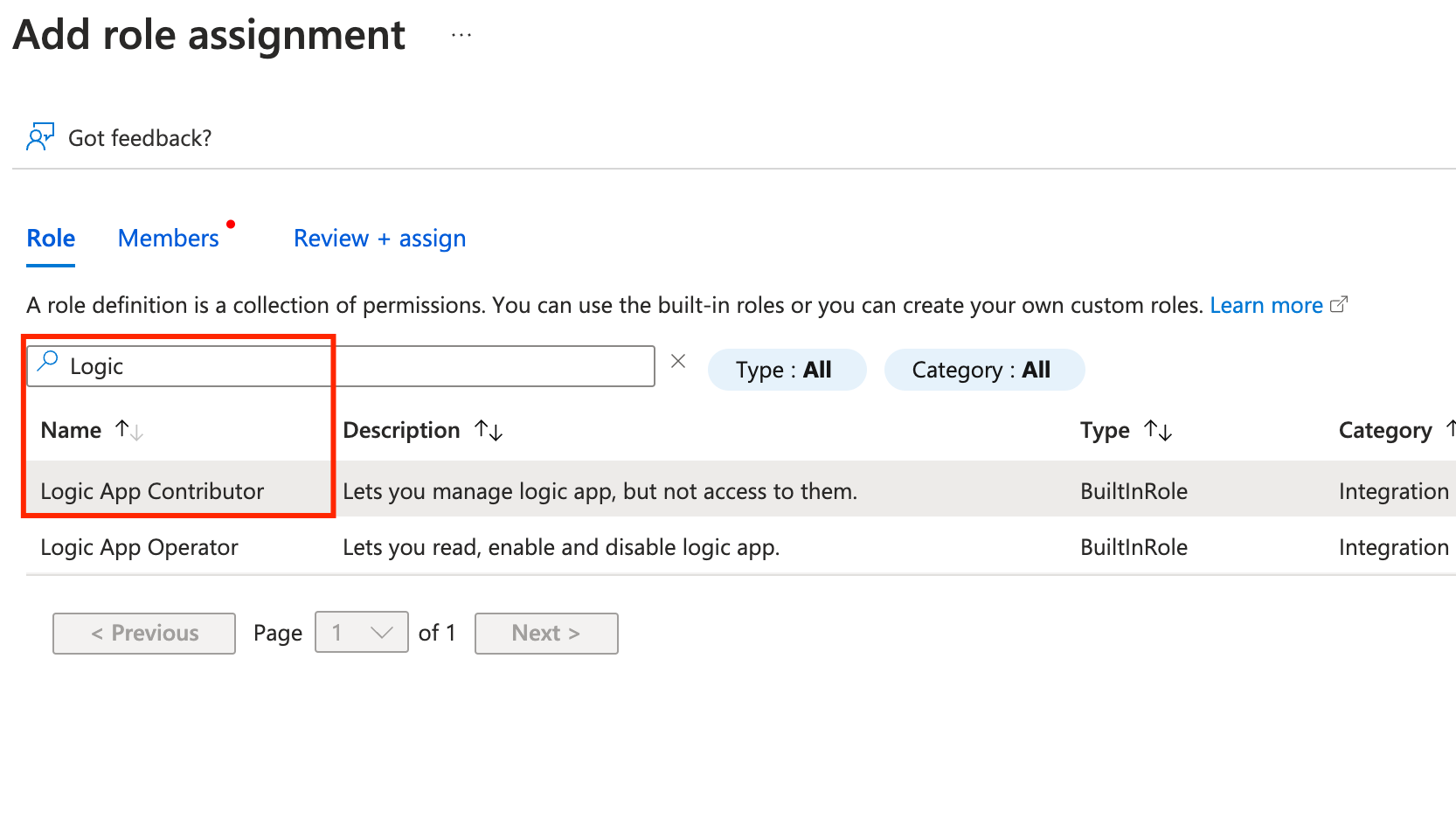
- Click on Owner Role and select the desired role. Click Next
-
Let’s make sure we have done it correcly: Click on the Check Access and confirm you have the 2 roles assigned.
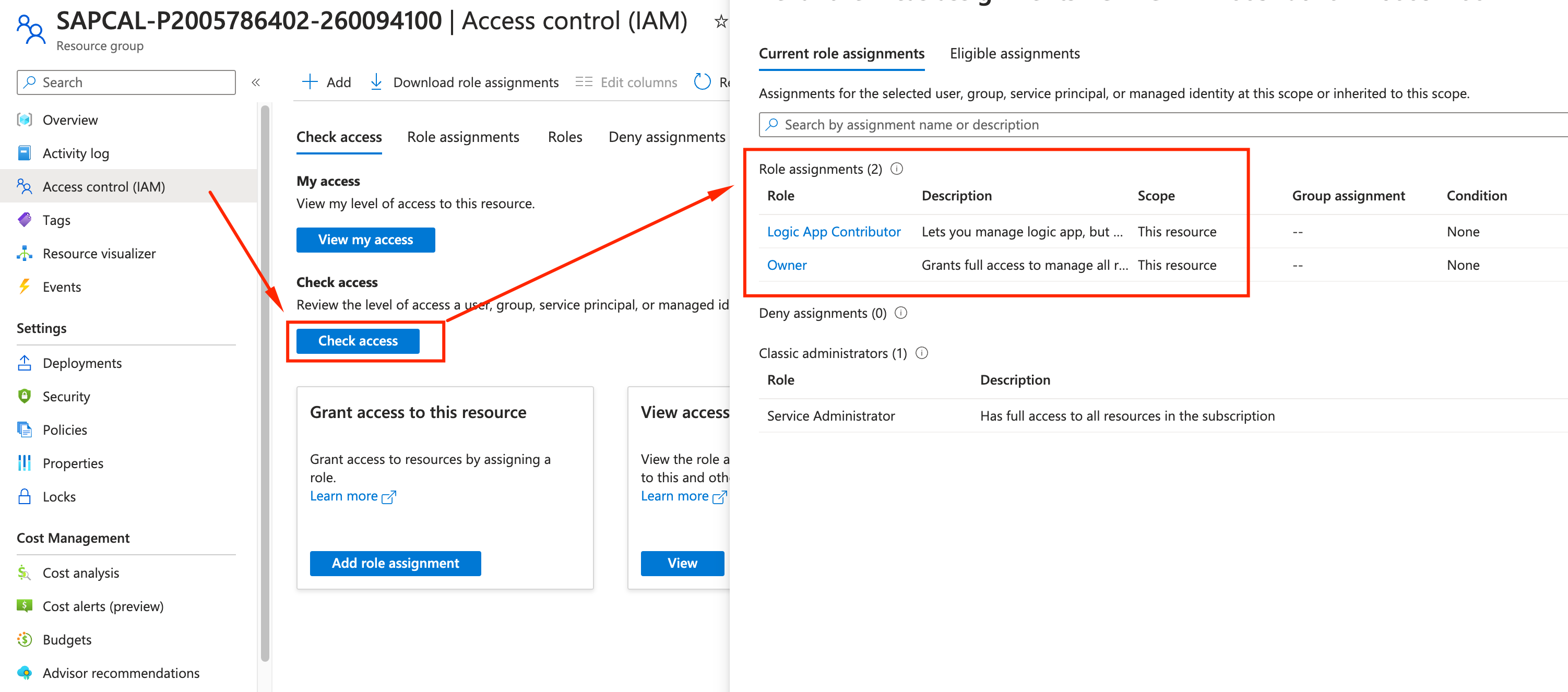
-
Then, go to Sentinel, click on Settings, then expand Playbook Permissions, click on Configure permissions and select the Resource Group . Click Apply.
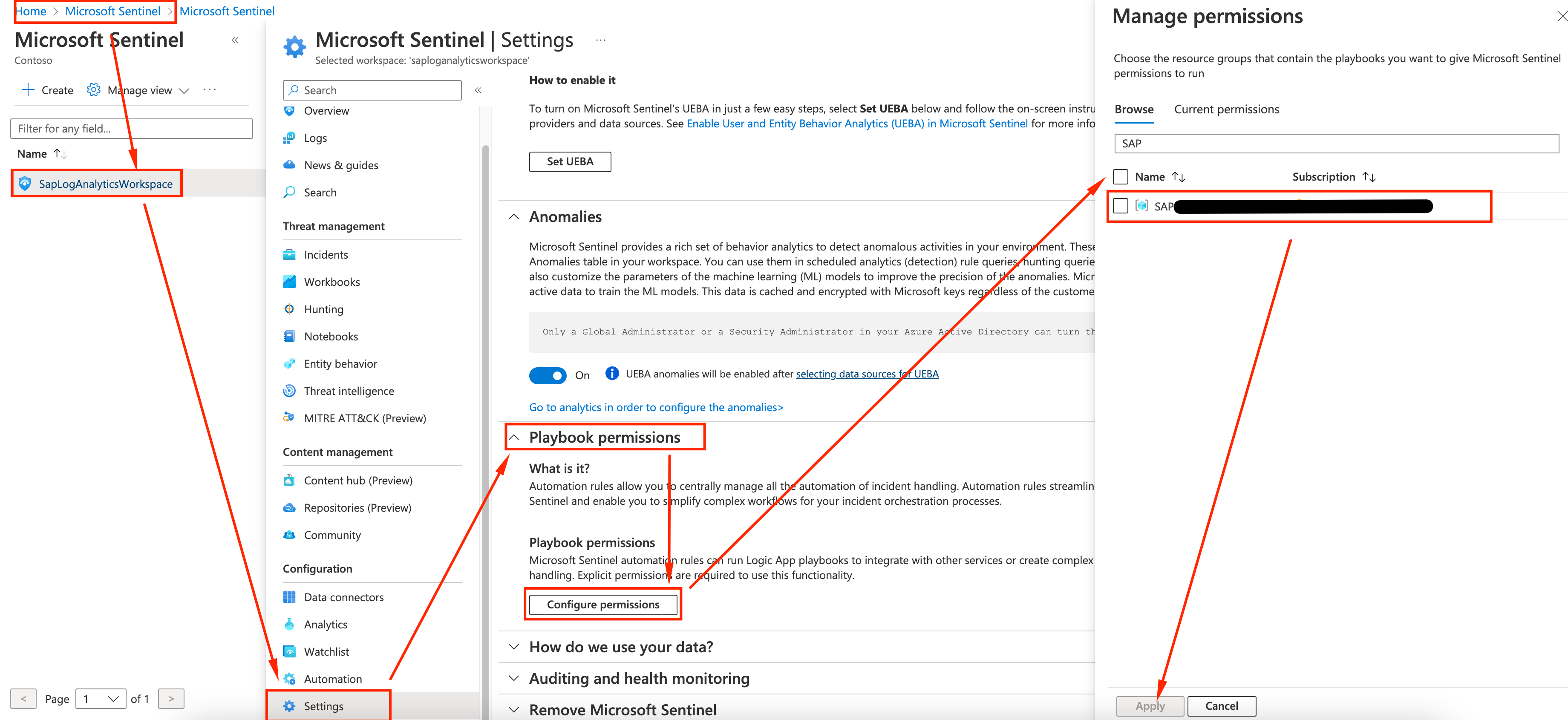
Creating our Automation
-
On the Sentinel page, under the Azure Portal, go to Automations, and Create a Playbook with Incident Trigger
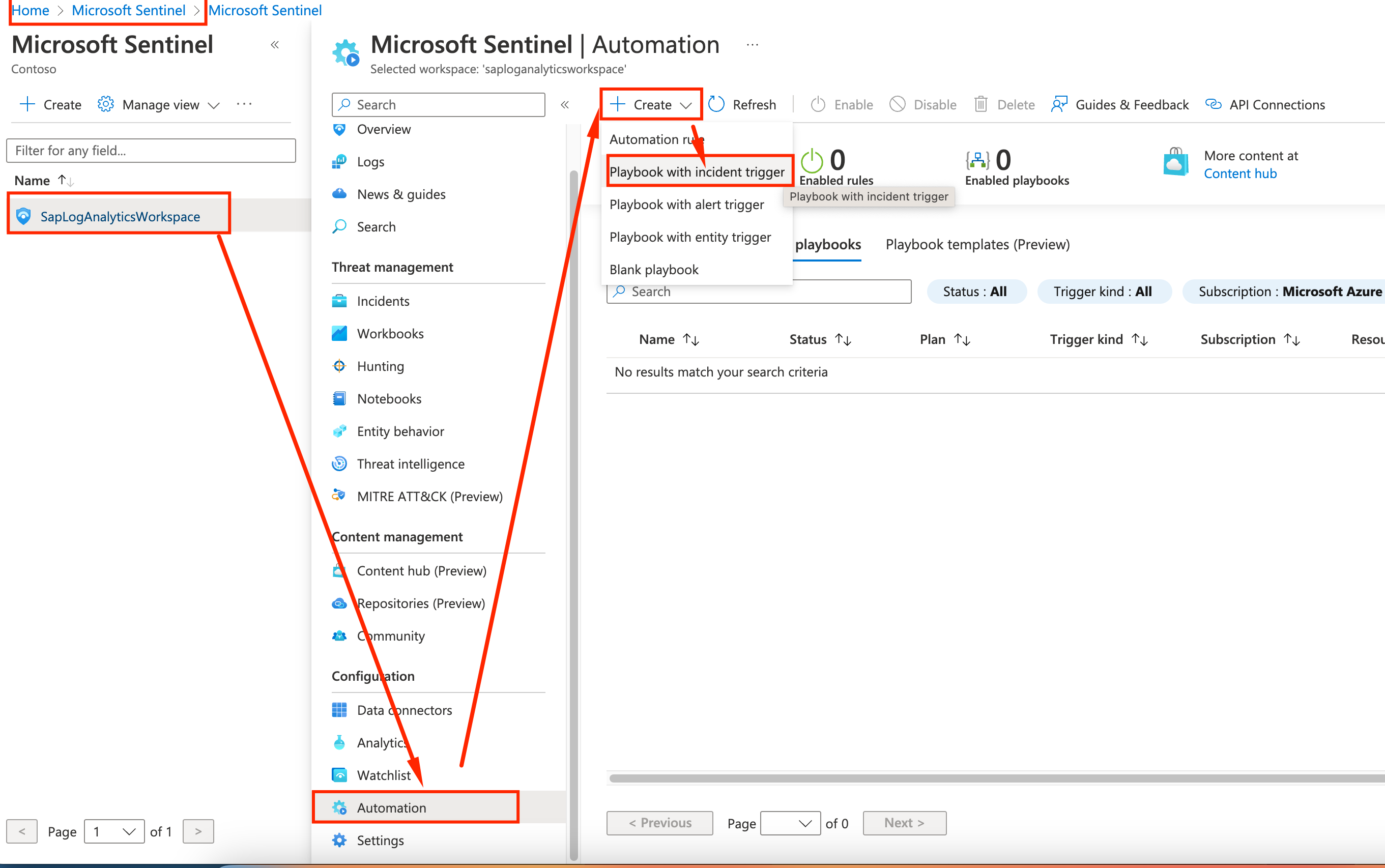
-
Pick the resource group and name the Playbook SAP_ADDGPTCOMMENTS, also make sure to check to enable diagnostics so you can troubleshoot any issues. Click Next: Connections
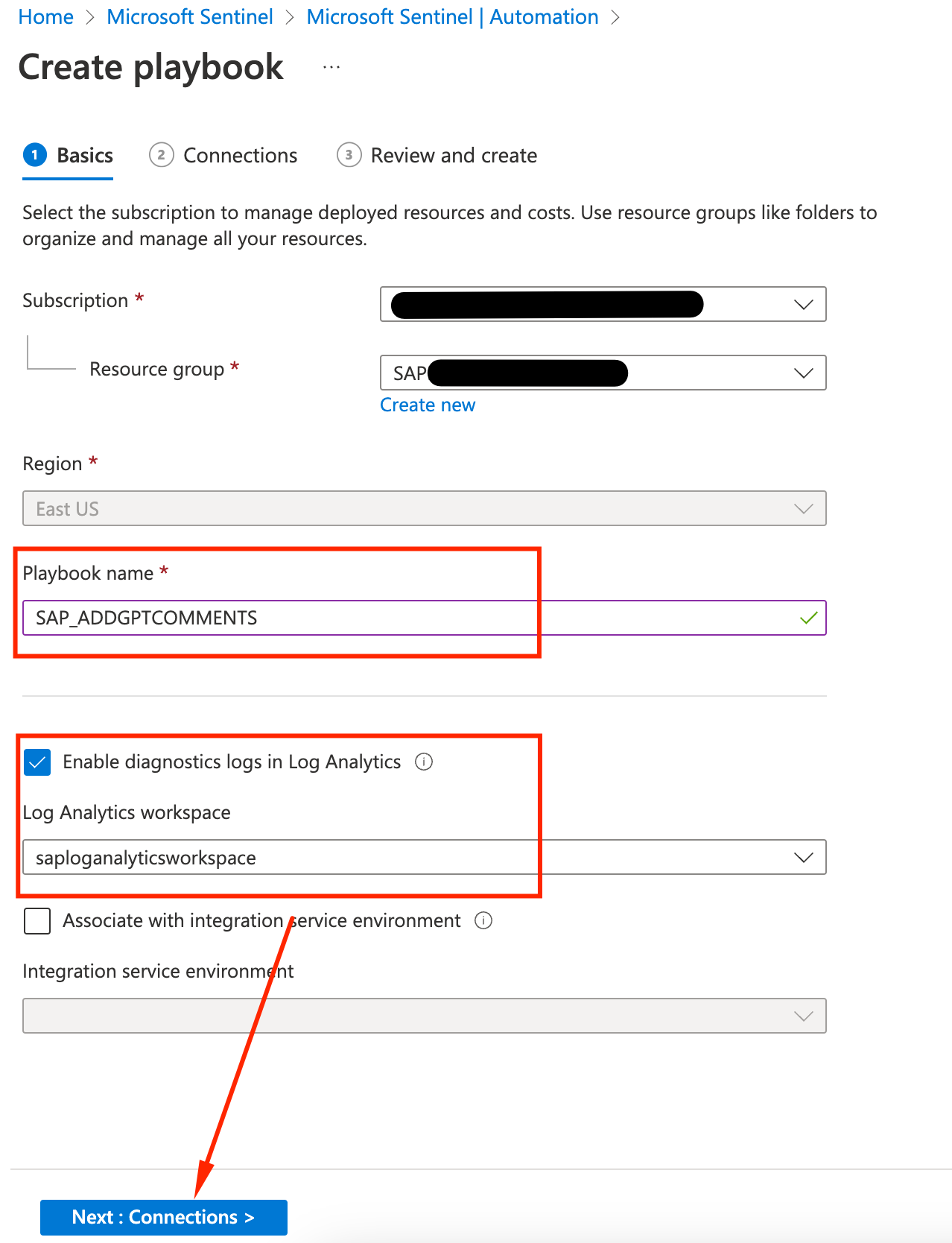
-
Permissions for Sentinel should be setup. We will further add permissions to the Logic App. Click Next: Review and Create
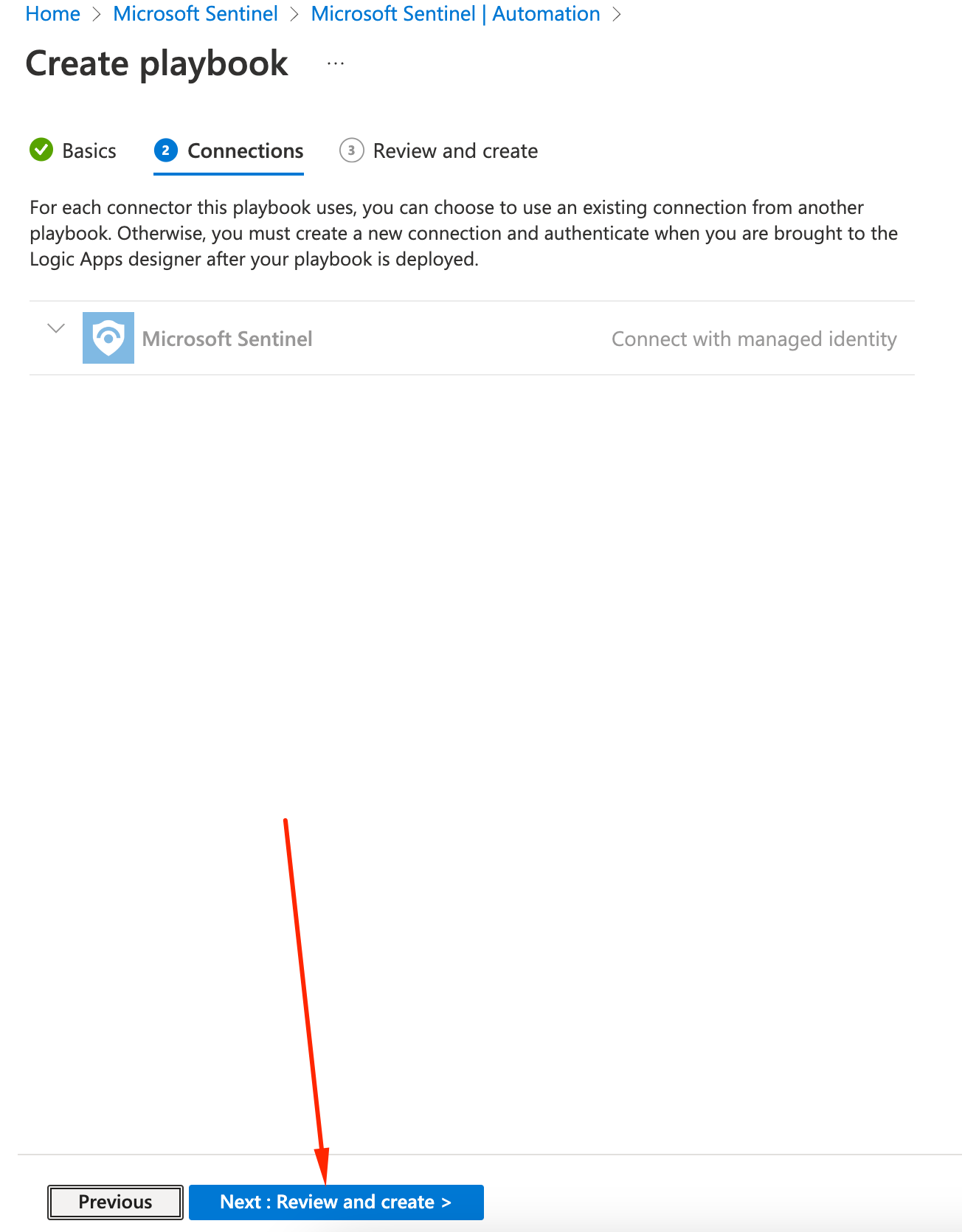
-
Click Create and continue to designer
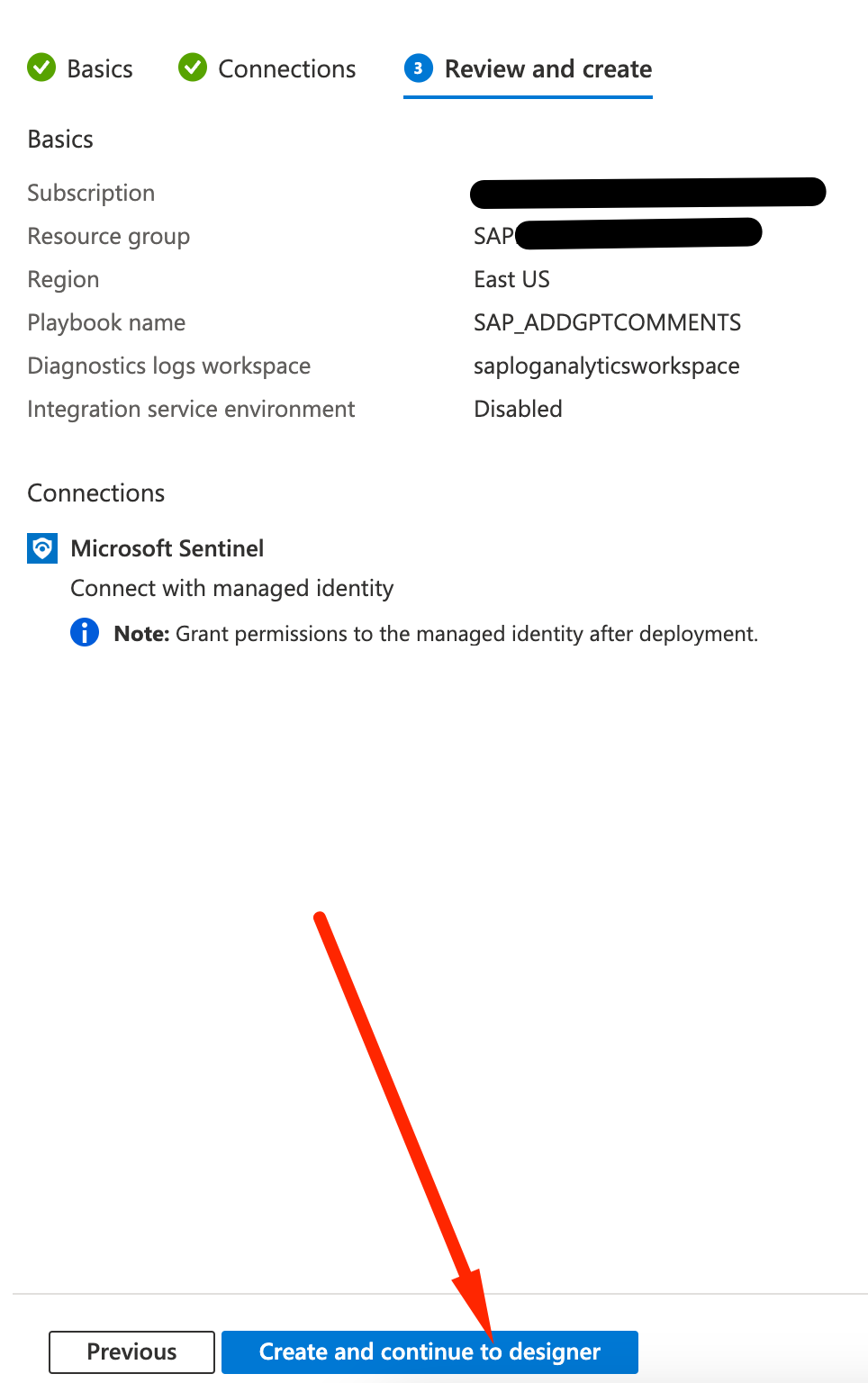
-
You will be brought to the Logic App Designer, where we will build the automation flow without creating a single line of code. It comes pre-populated with a Sentinel Incident as trigger. let’s add the GPT3 action. Search for GPT3 and select GPT3 completes your prompt action:
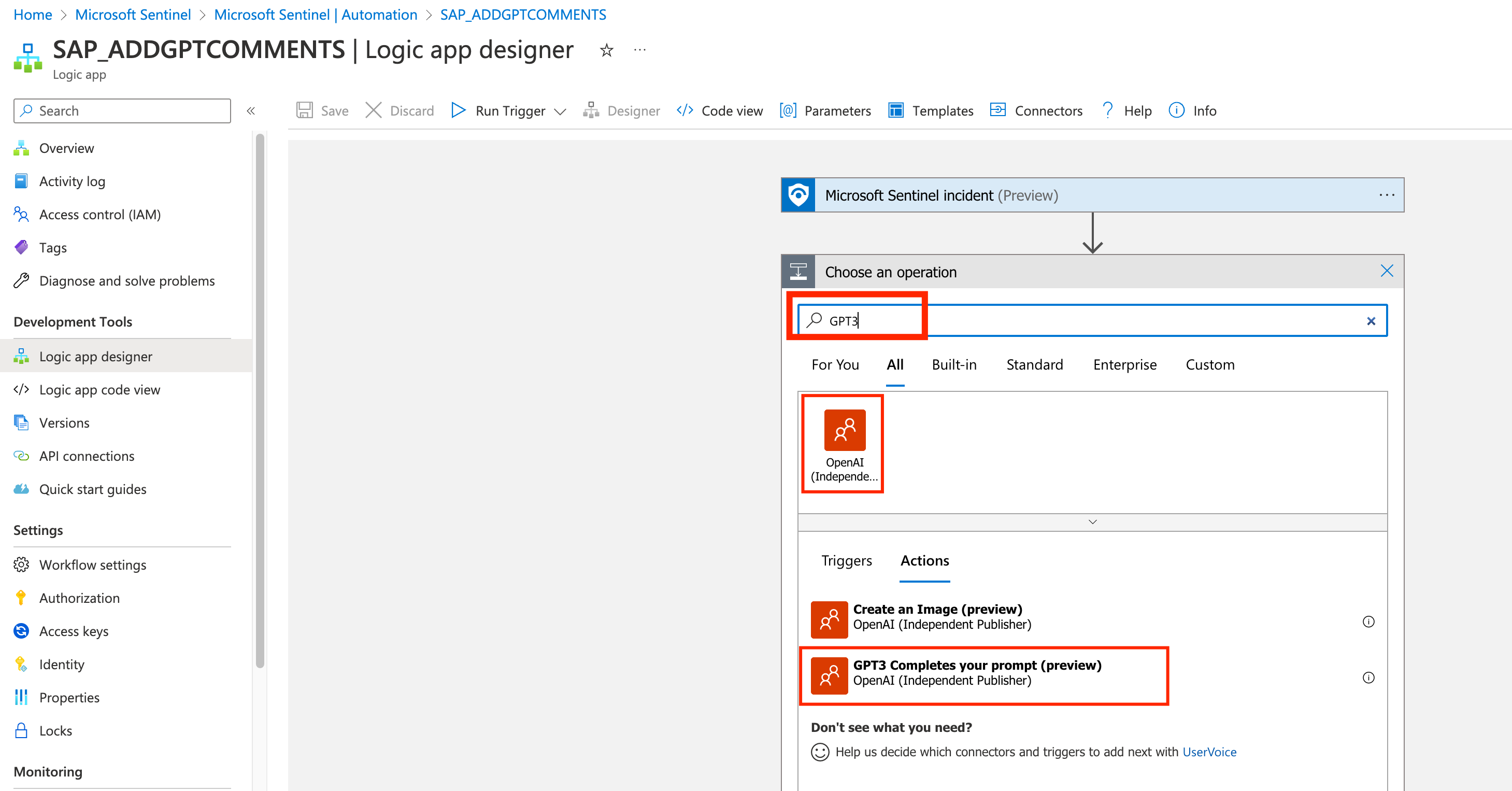
-
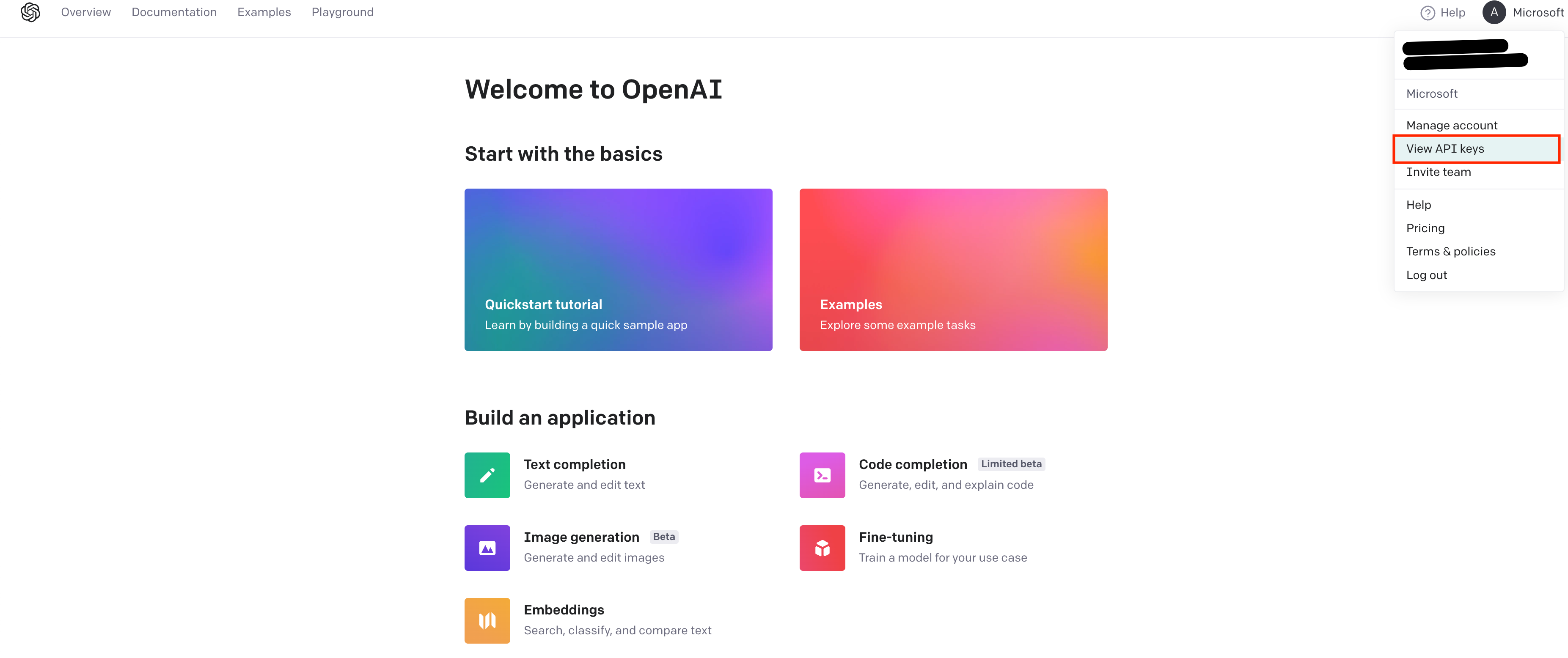
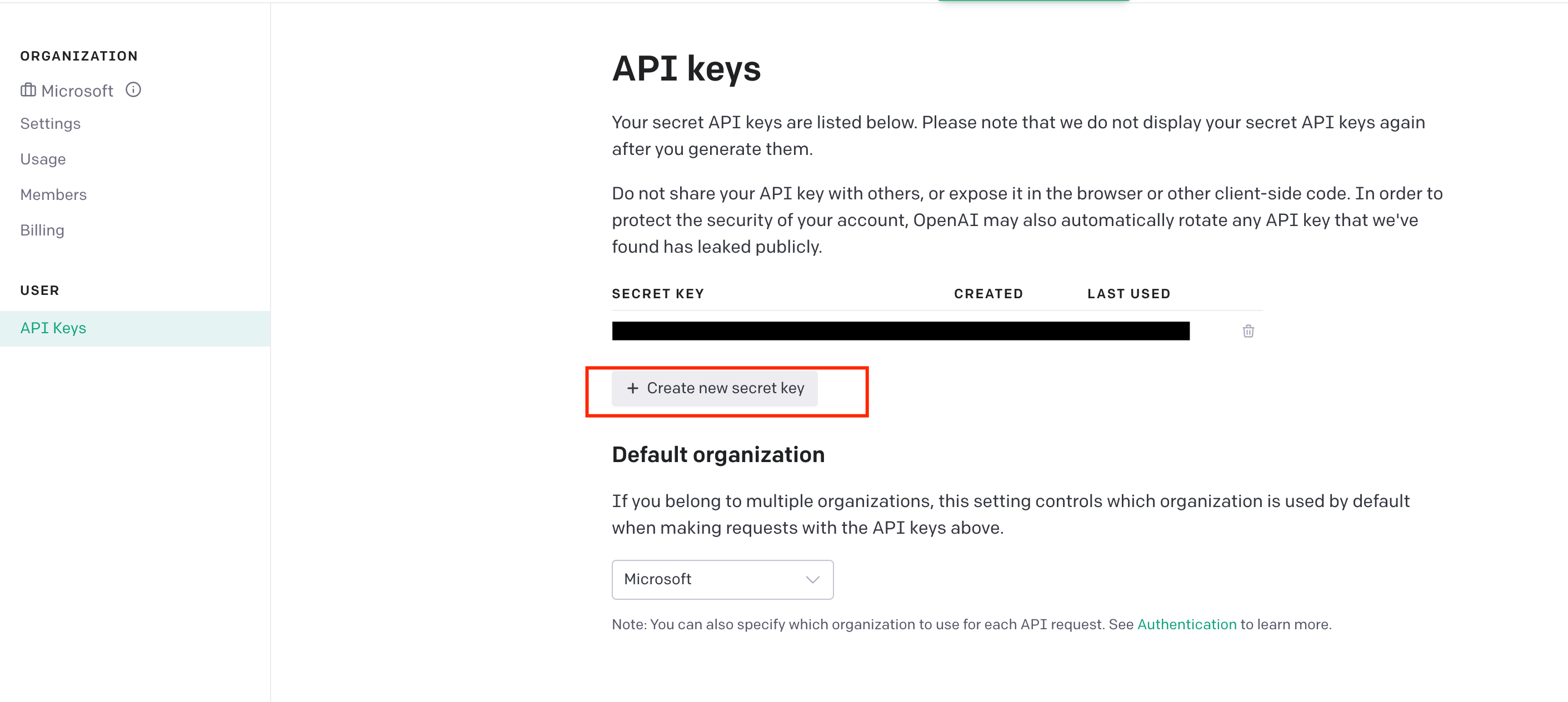
Then you will need to provide an API Key for OpenAI GPT3. Log in (or create an acount) in the OpenAI page, on the top right click on your user and View API Keys and then Create a secret key. Copy the value for the next step.
-
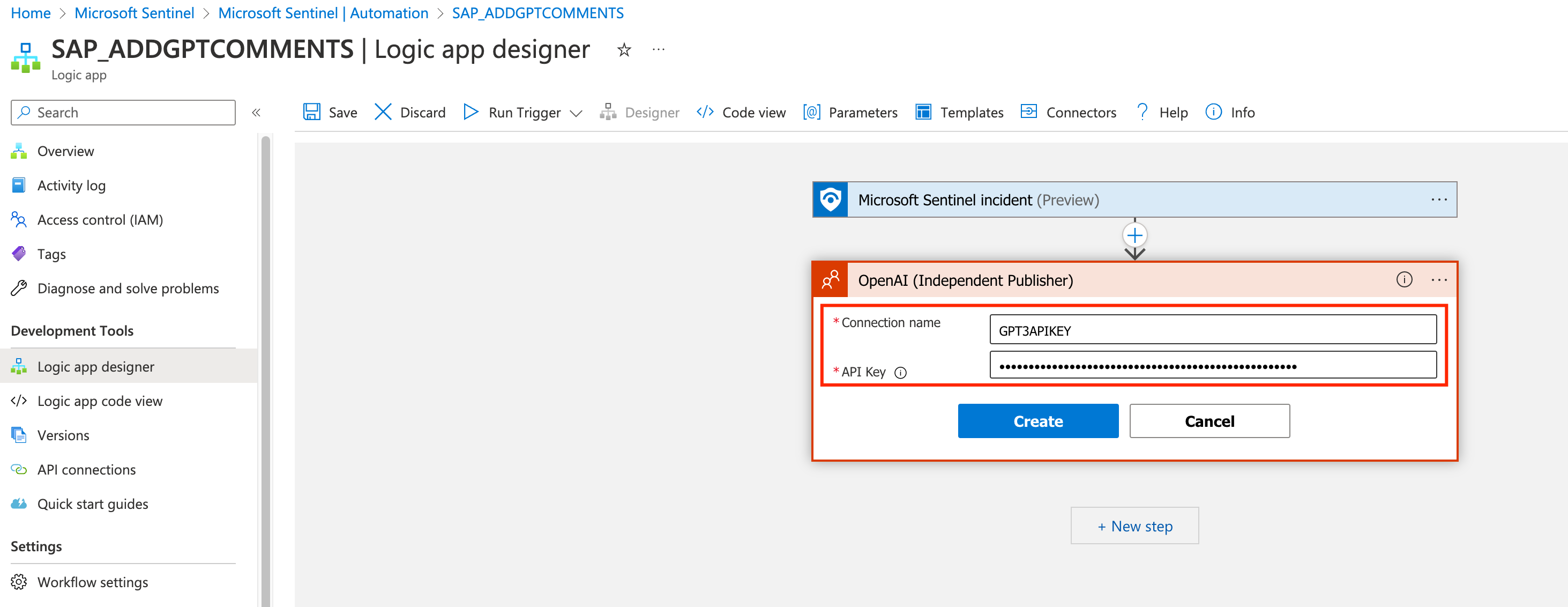
Back to the Logic App, name the connection as GPT3APIKEY and add you key in the format Bearer (example “Bearer djklcsjcsdkjcsdlkcsjdlcsd”). Click Create.
-
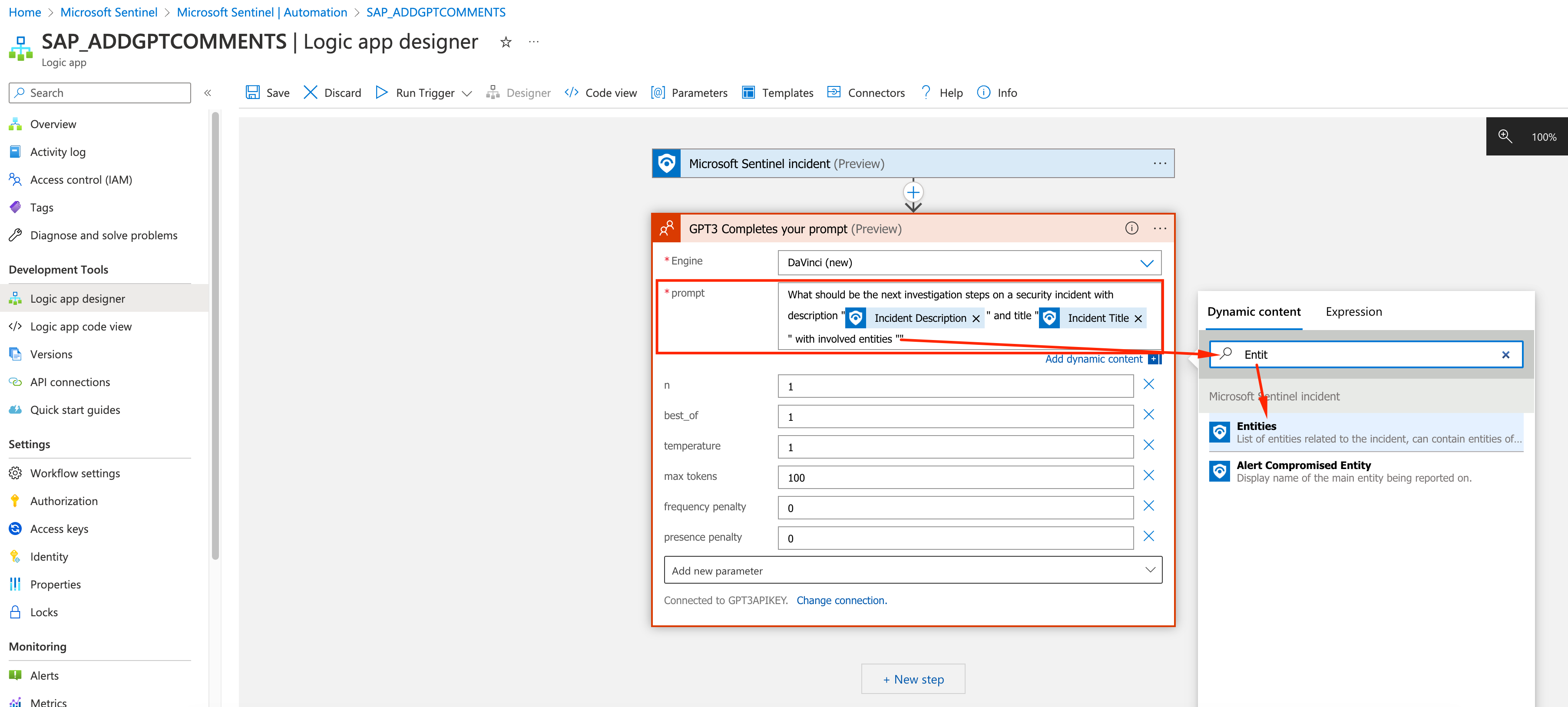
Let’s add the prompt we need using the data from the Sentinel incident.
- Prompt: “What should be the next investigation steps on security incident with description “” and title “” with involved entities “”
- Dynamic Content: Incident Description, Incident Title, Entities
- You can also expand max tokens from 100 to 250
-
As a next step, we will tell to Logic Apps what to do with the GPT3 API response. Add an action Add comment to incident v3 under Sentinel.
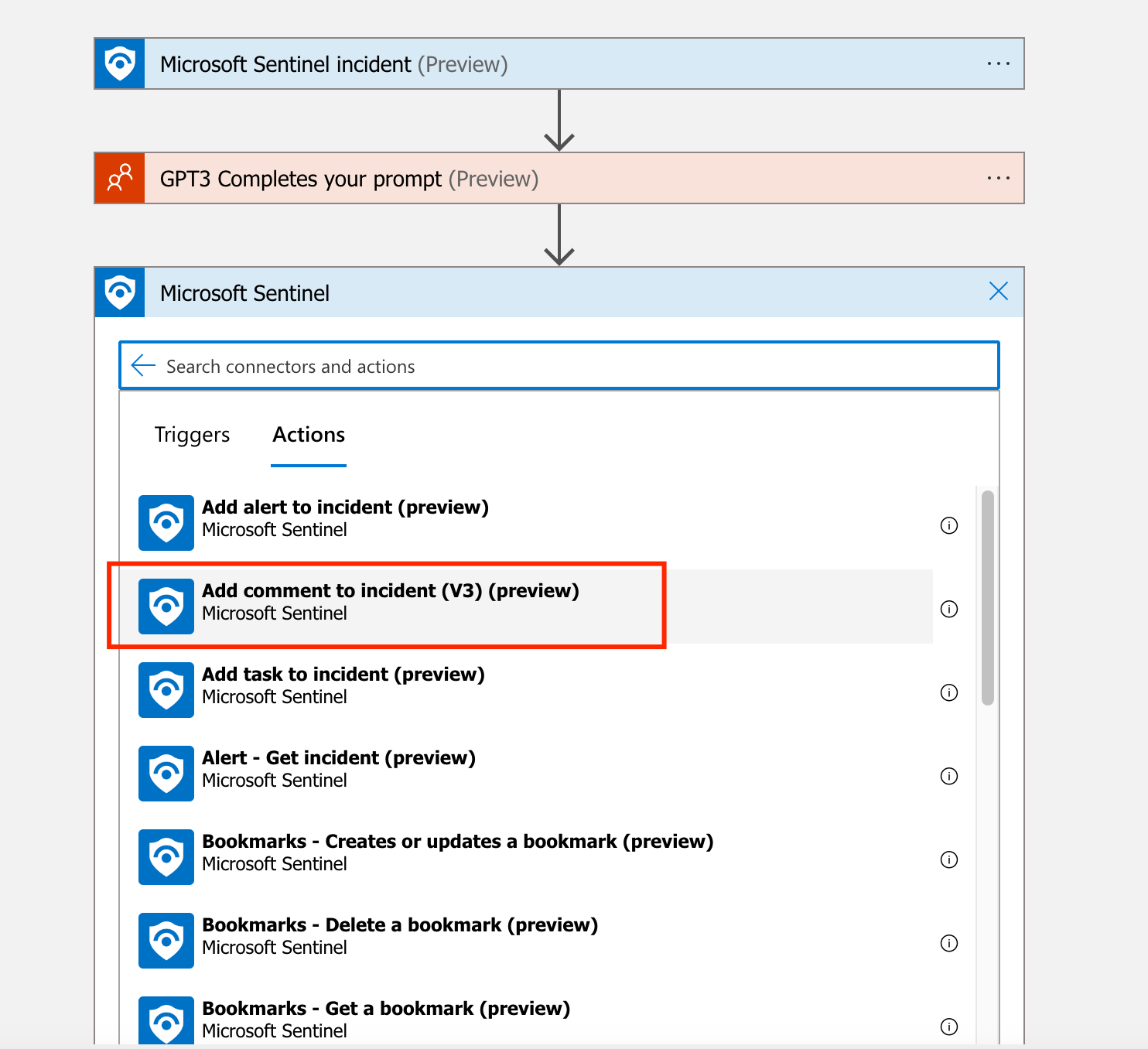
-
Use the Dynamic Content for Incident ARM ID and expand GPT3 dynamic content and select Text.
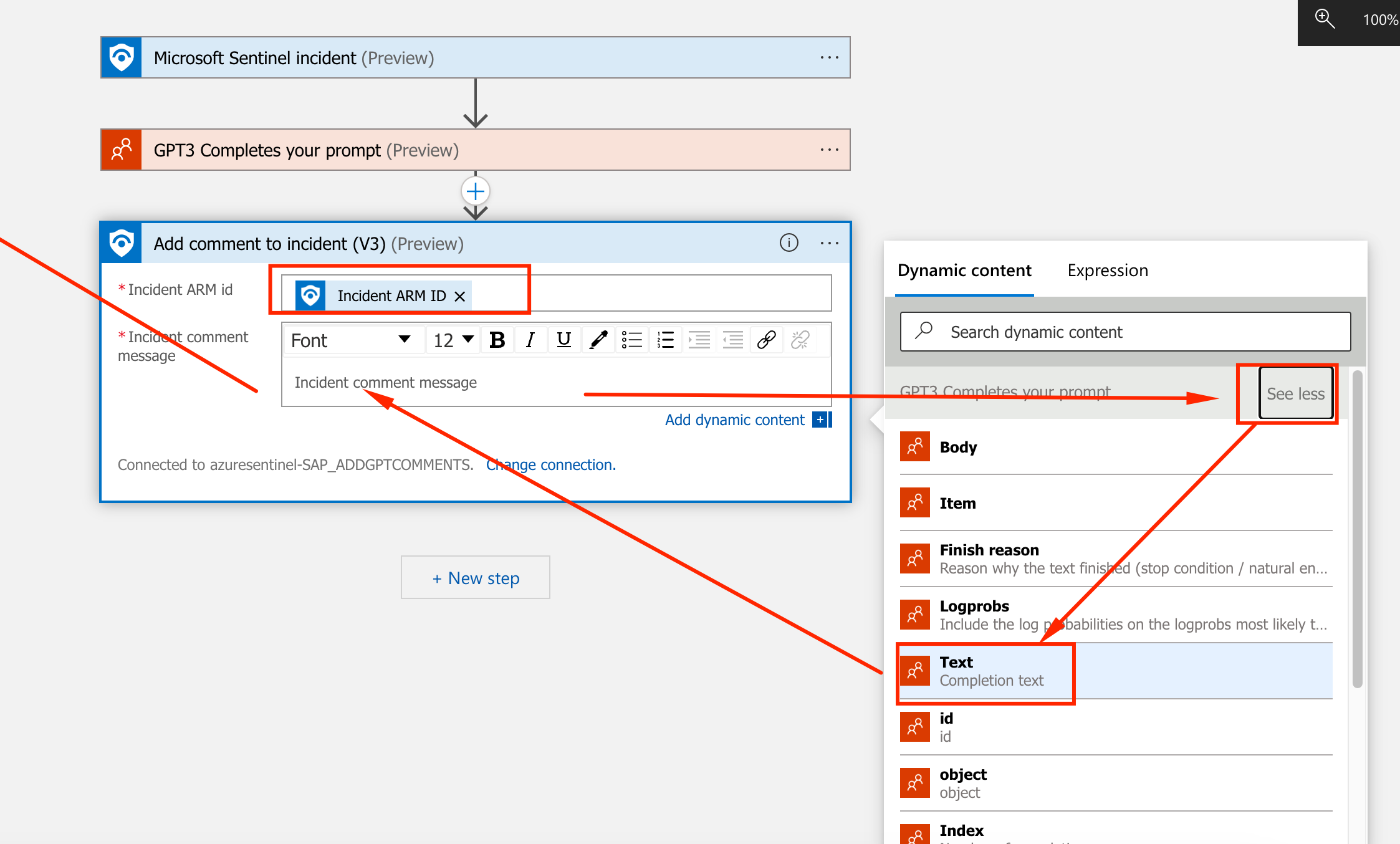
-
That is it, the Logic App is setup. It should be something like the picture below:
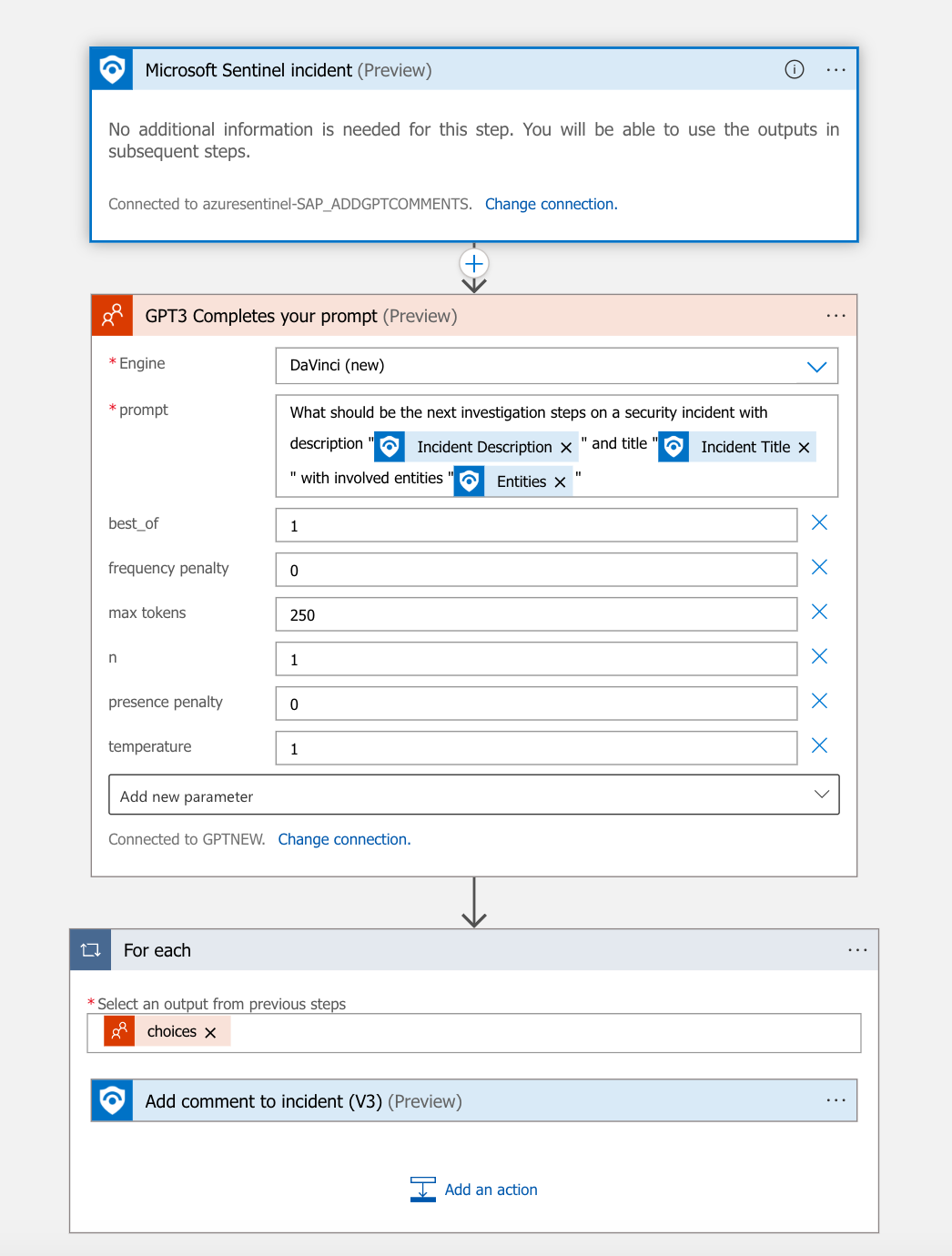
-
With our Logic App ready, we need to allow it to act on the Resource Groups resources. Still on the Logic App page, go to Identity, enable Status and click on Azure role assignments.
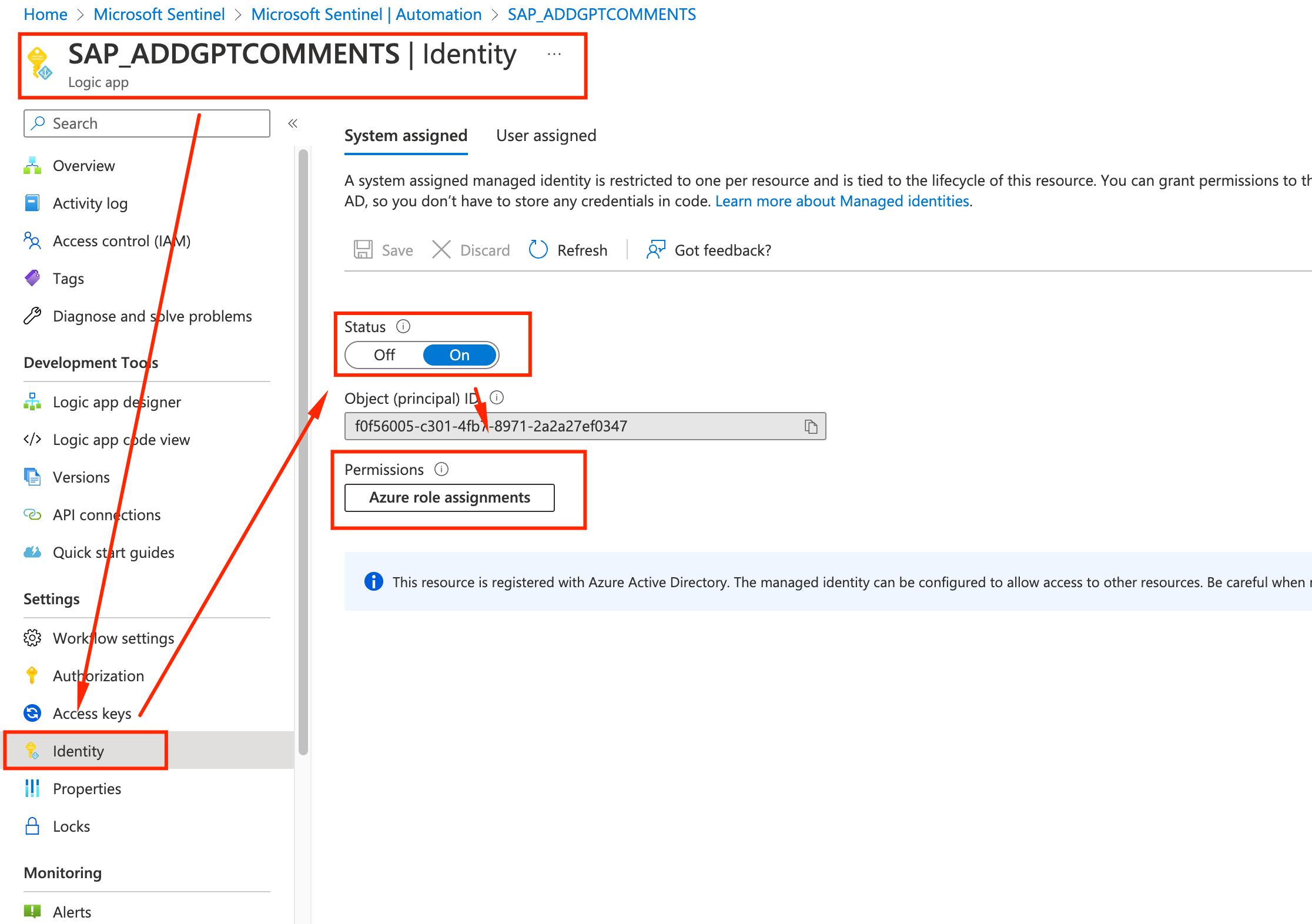
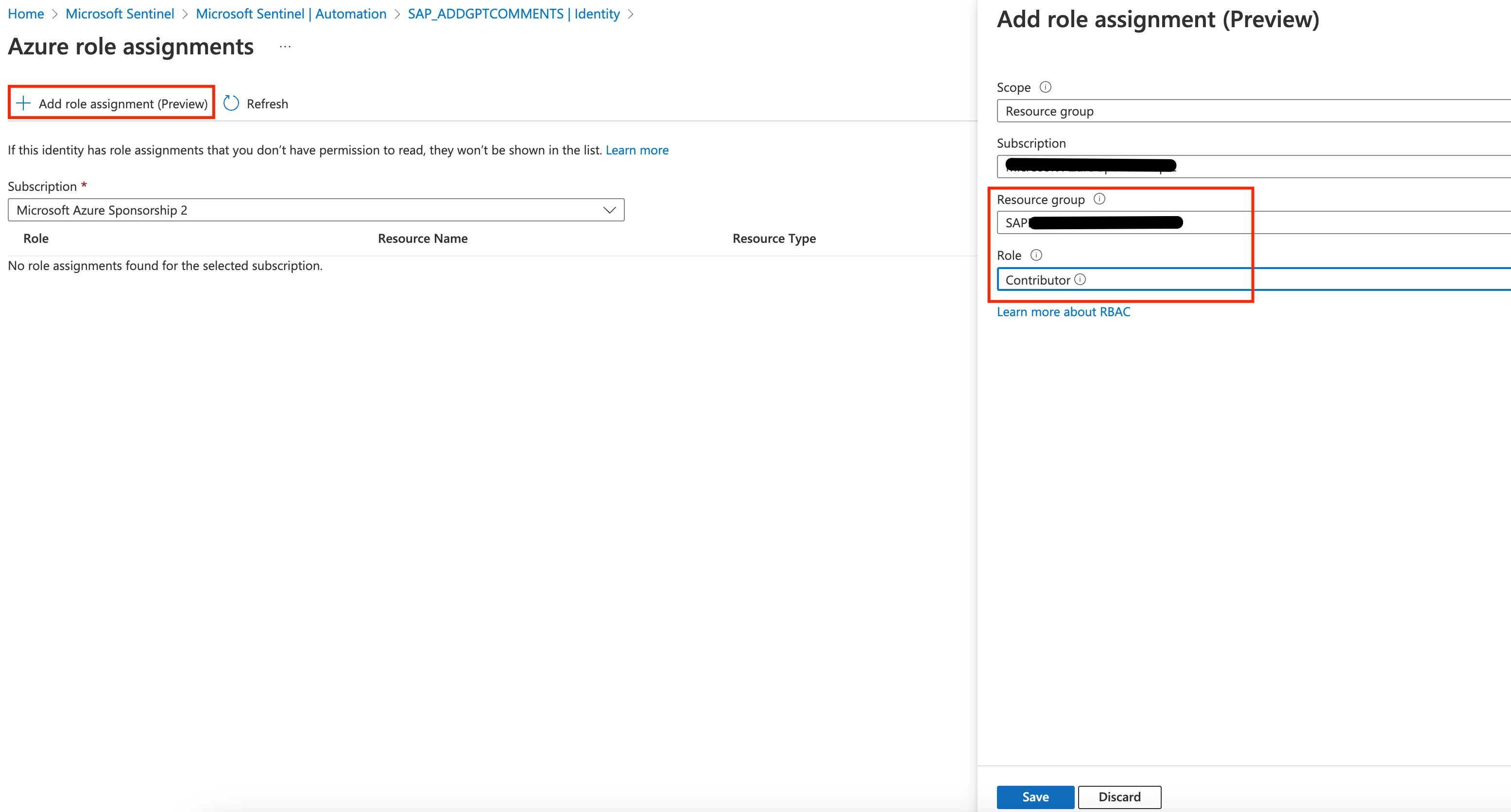
-
Click on the Add role assignment button and specify that you want to grant permissions based on Resource Groups, selecting resource group and the Contributor role. Click Save and we are done in the Logic App page.
-
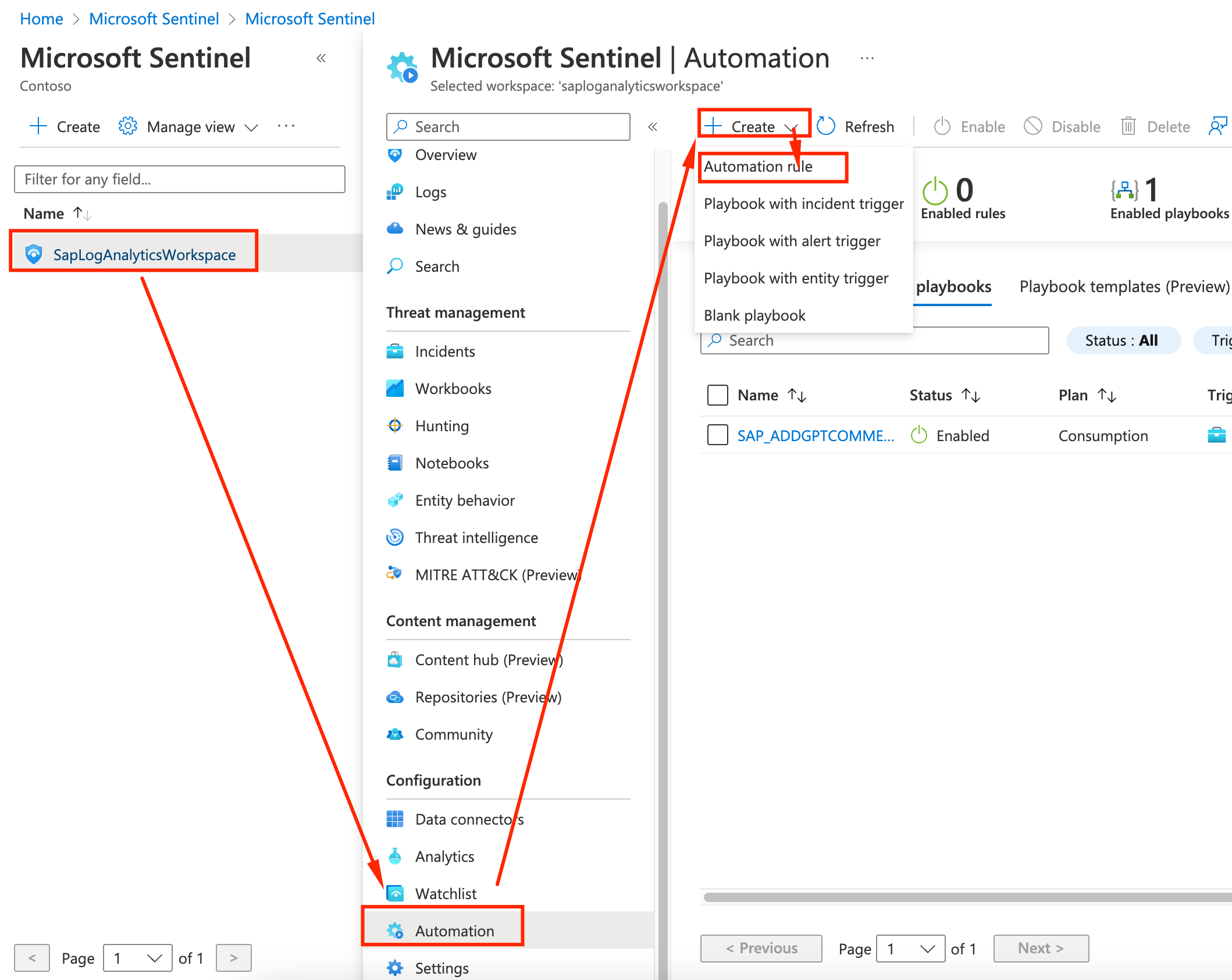
Go back to Sentinel page, and let’s set up a rule triggering the Logic App we just created. CLick on Automation and create an Automation rule.
-
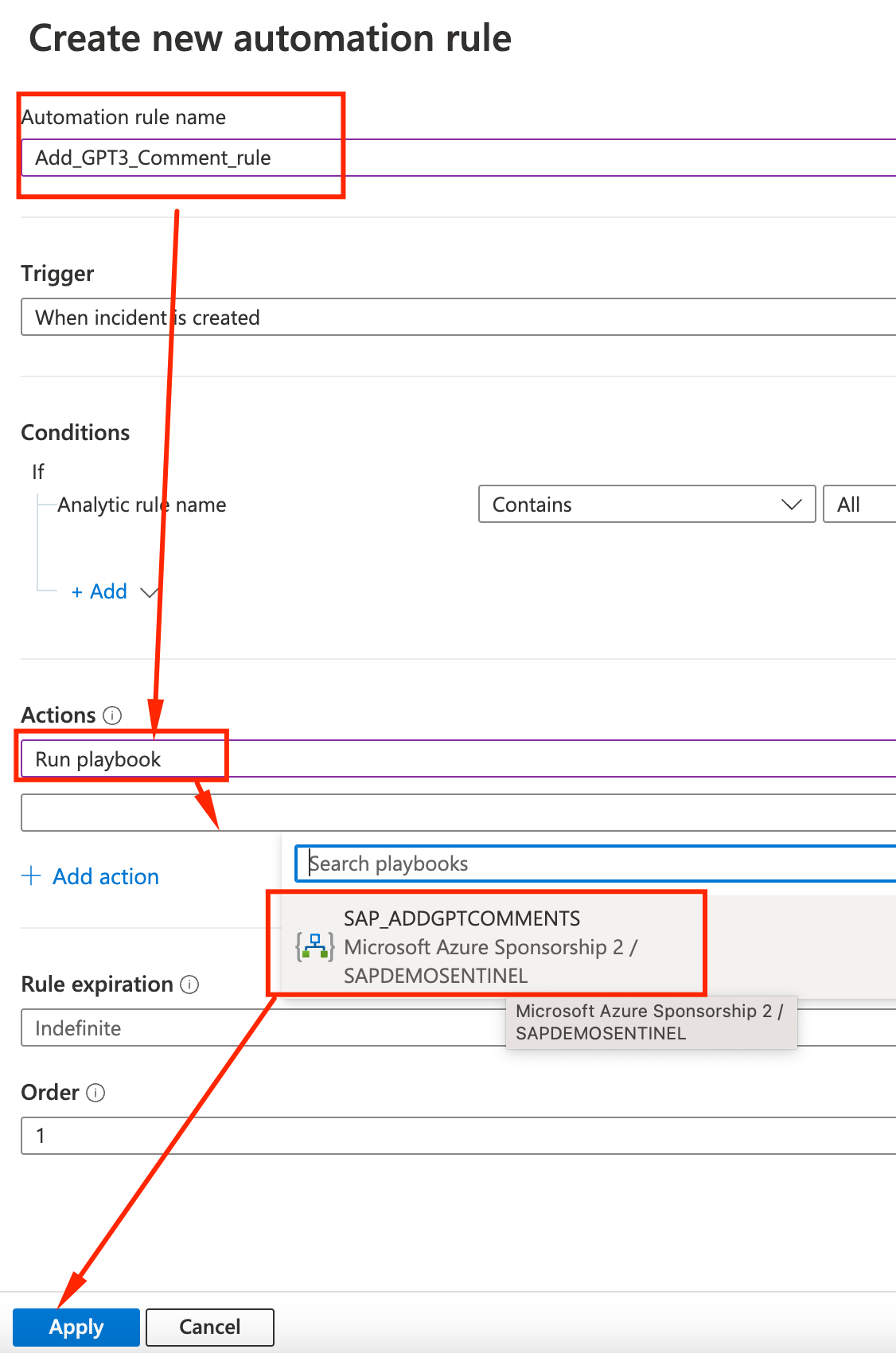
Let’s name the rule Add_GPT3_Comment_rule, select as Action Run playbook and select the previously created SAP_ADDGPTCOMMENTS playbook. Click Apply
And that is it. We should have setup everything so that when an alert shows up and an incident is created, Sentinel will be able to append comments with additional incident information for first responder. Let’s test it !
Generating an Incident
-
Log on to the Bastion Host and log on the SAP GUI (SAP Logon) with user SAP/Welcome1* (this will be a super restricted user log in incident)
-
Go to TCODE SU01 so we can create a new user
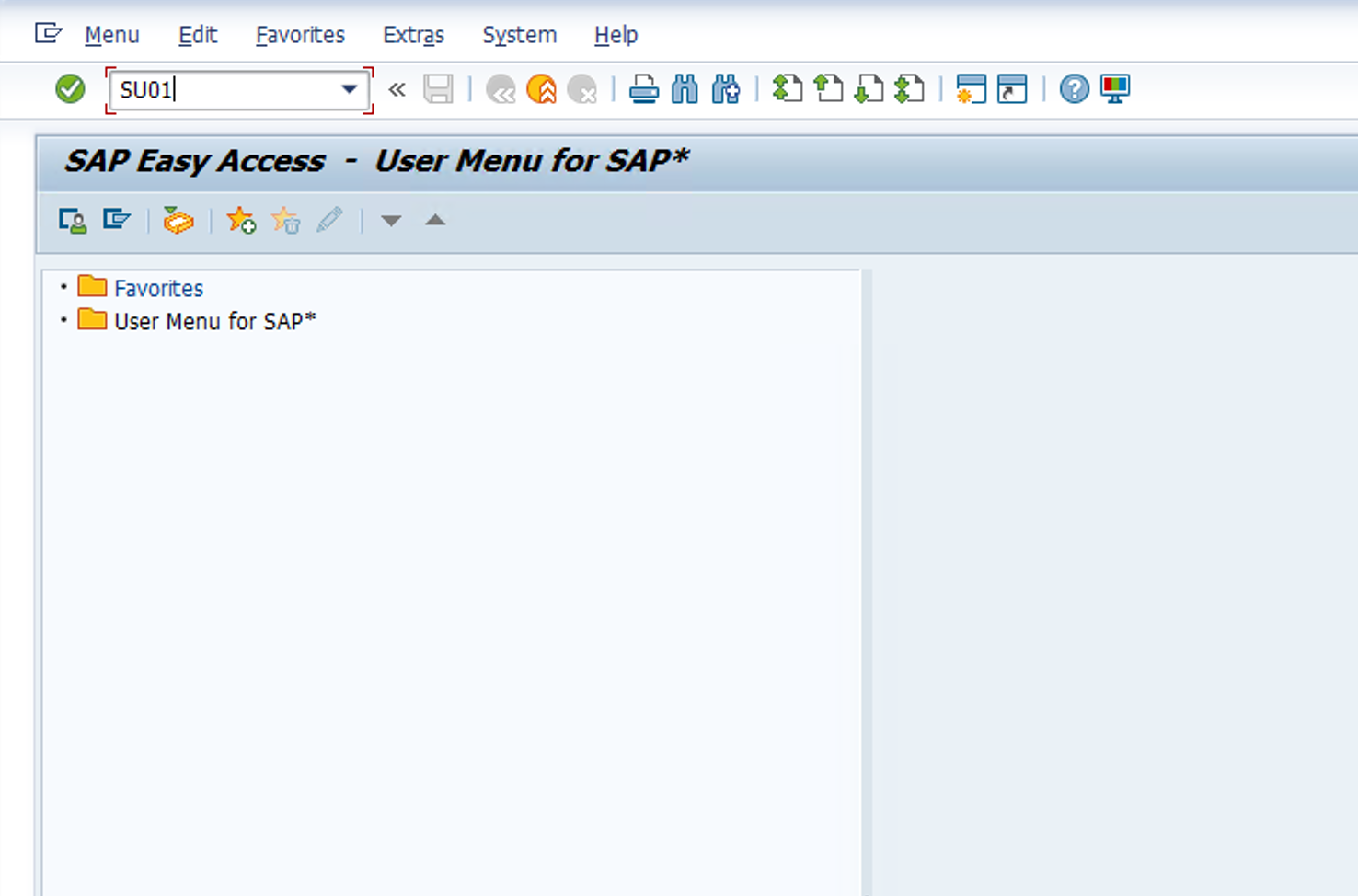
-
Name the user hacker01 and click on User
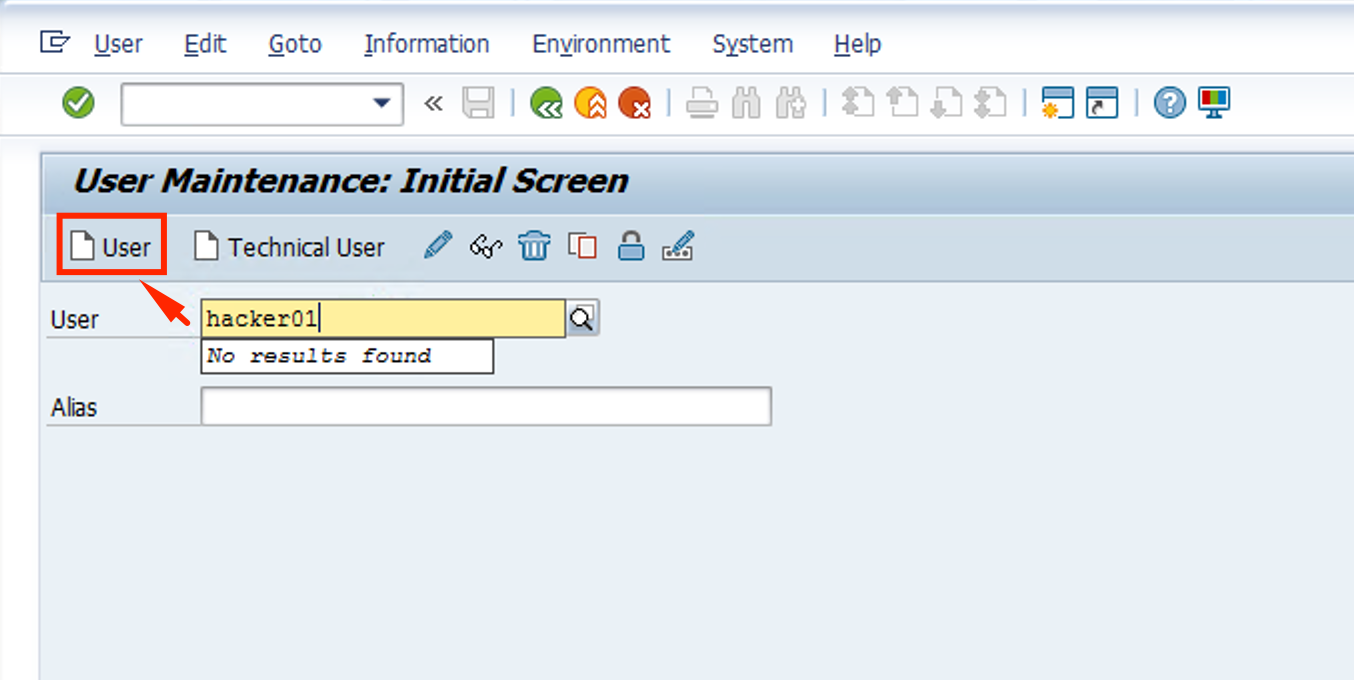
-
Give it a Last Name hacker01 and move on to the Logon Data tab
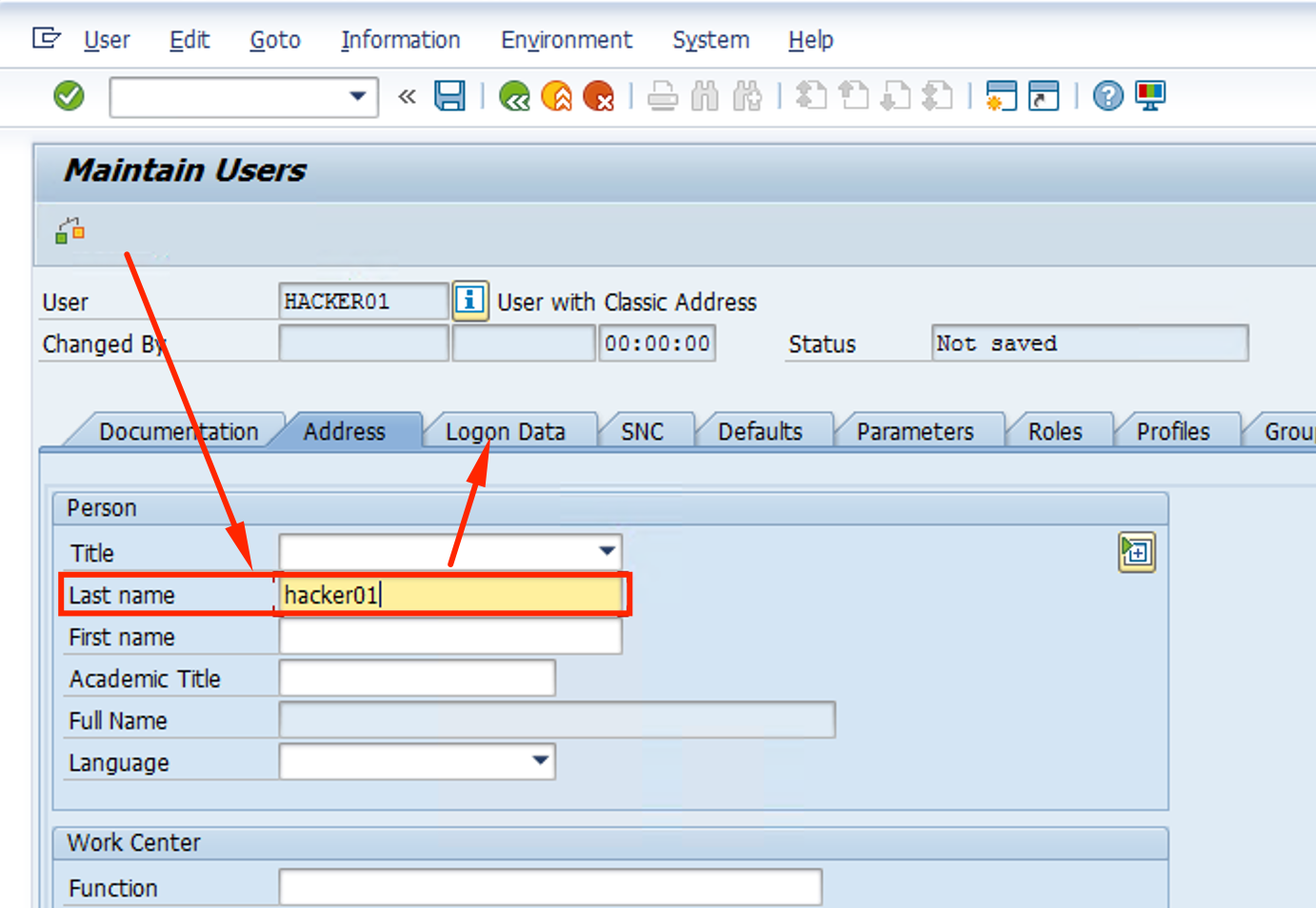
-
Set the password and confirm to Welcome1, c;lick Save and then log off be using the Back button
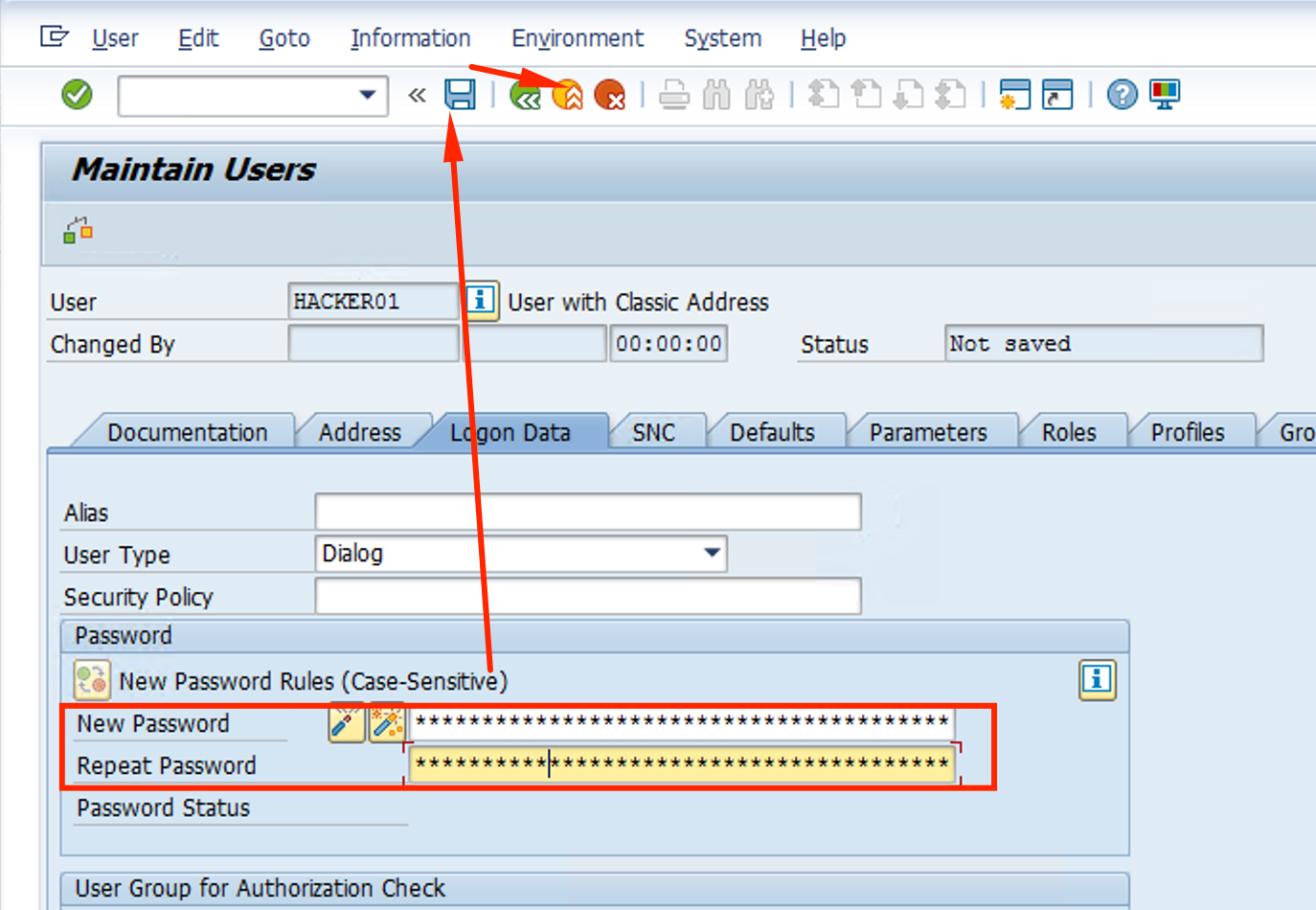
-
Now, lets log in with the newly creater hacker01/Welcome1 user, simulating another security incident
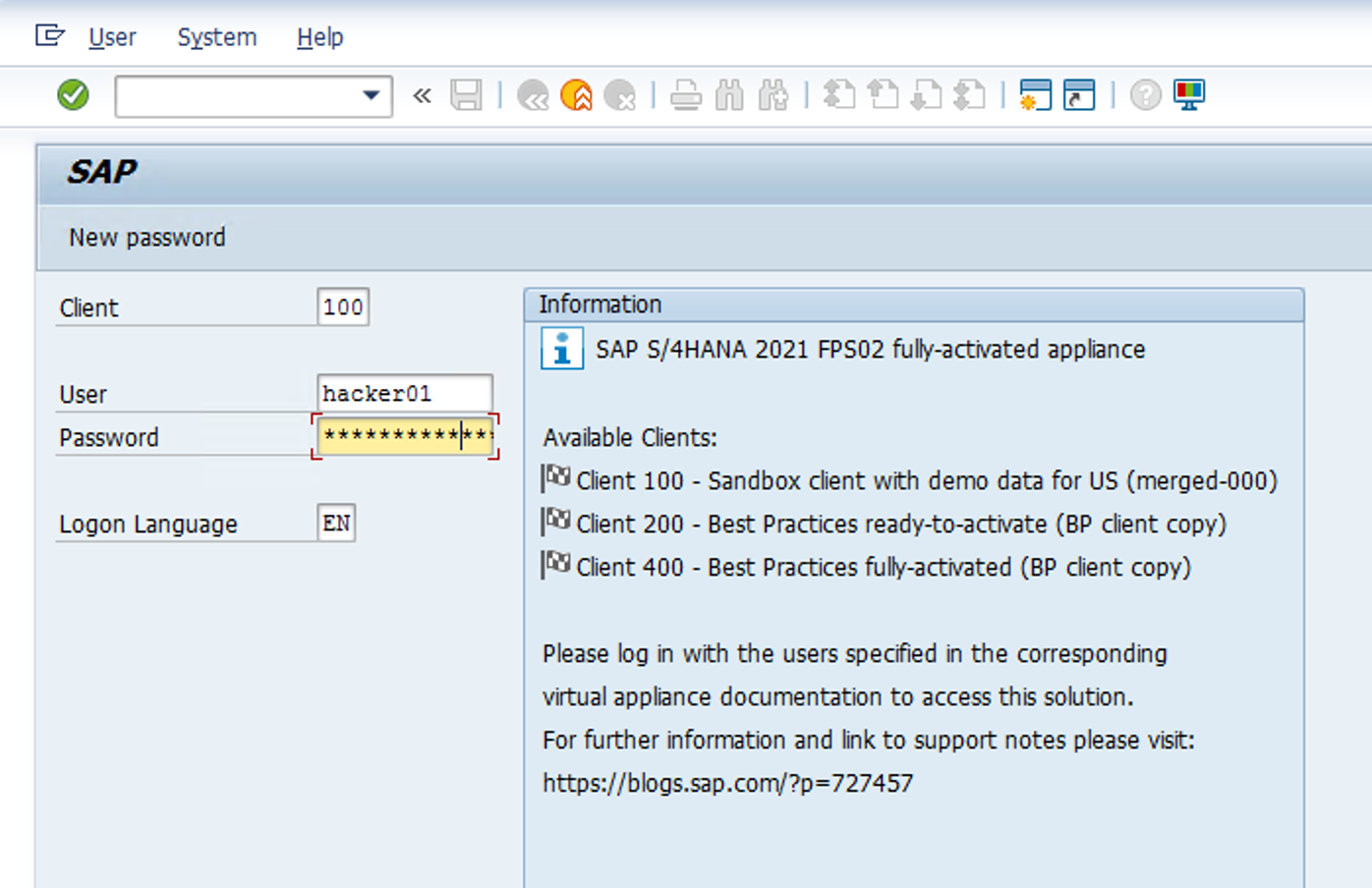
-
It will ask for a new password. You can use Microsoft1 and the new one here and proceed. Once logged in, you can log off, since the risk was already been recorded.
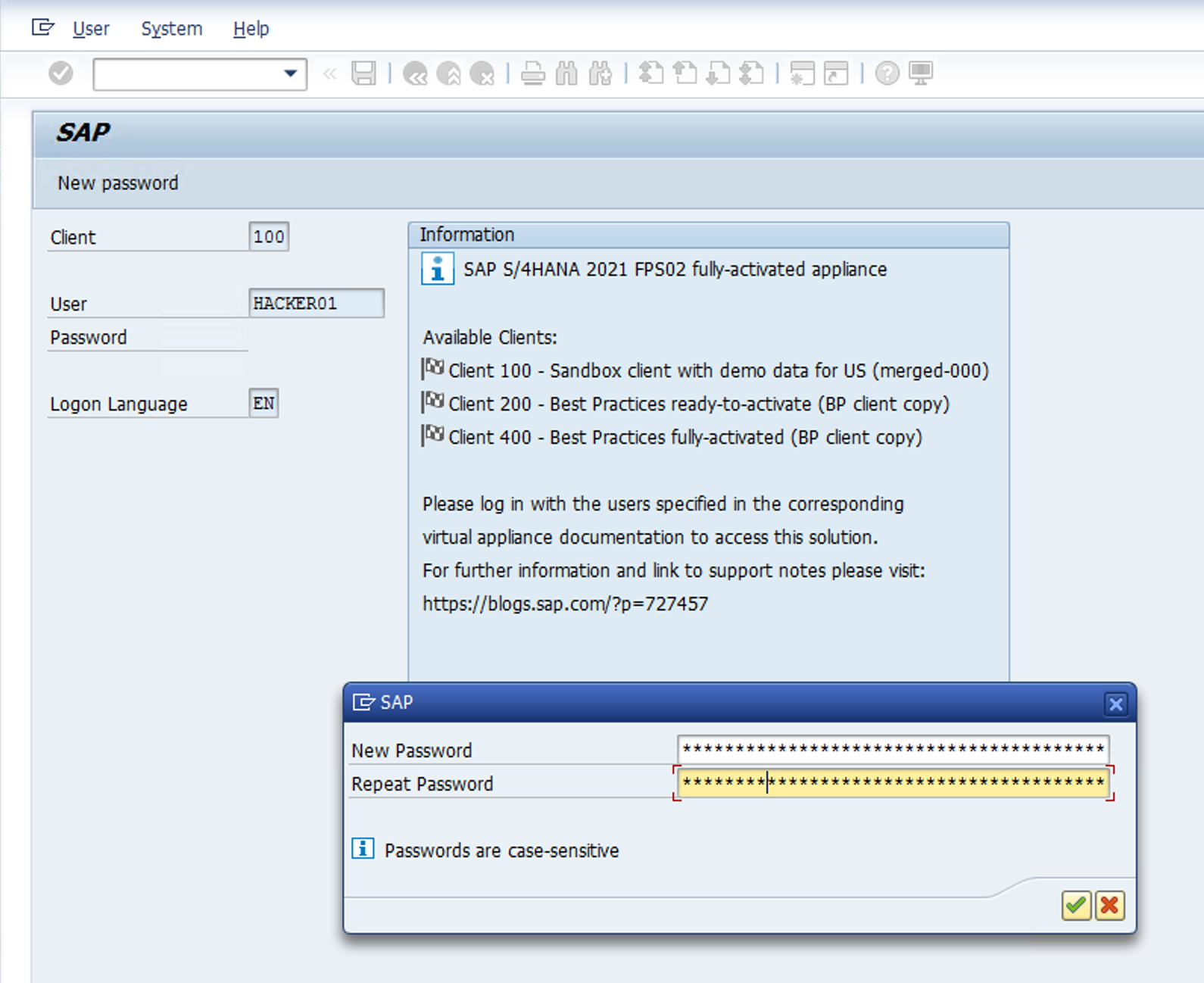
-
After a few minutes (5-10 minutes) the logs should have flown to Sentinel and an Incident should have been created. Go to Sentinel, on Overview (optionally you can disable the new interface), and select one recent incident.
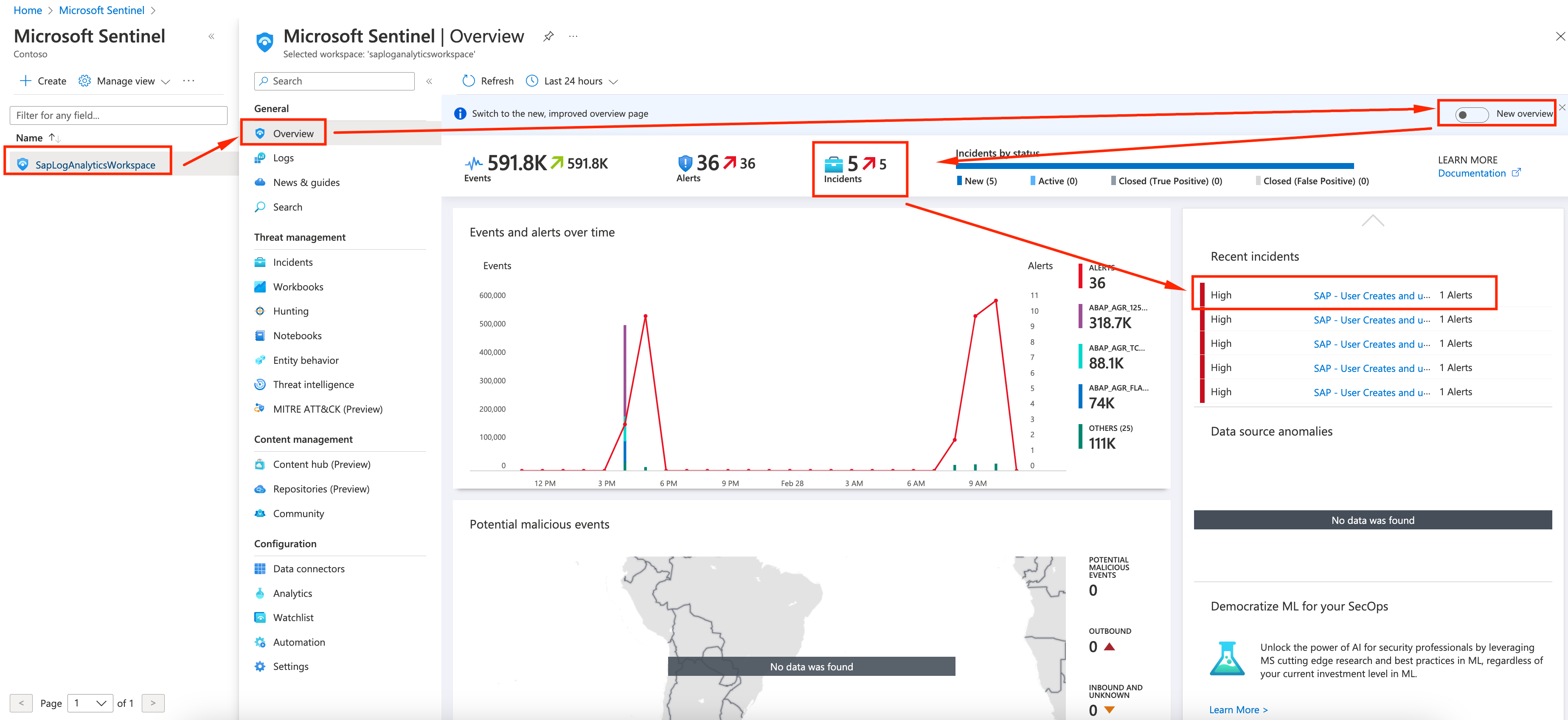
-
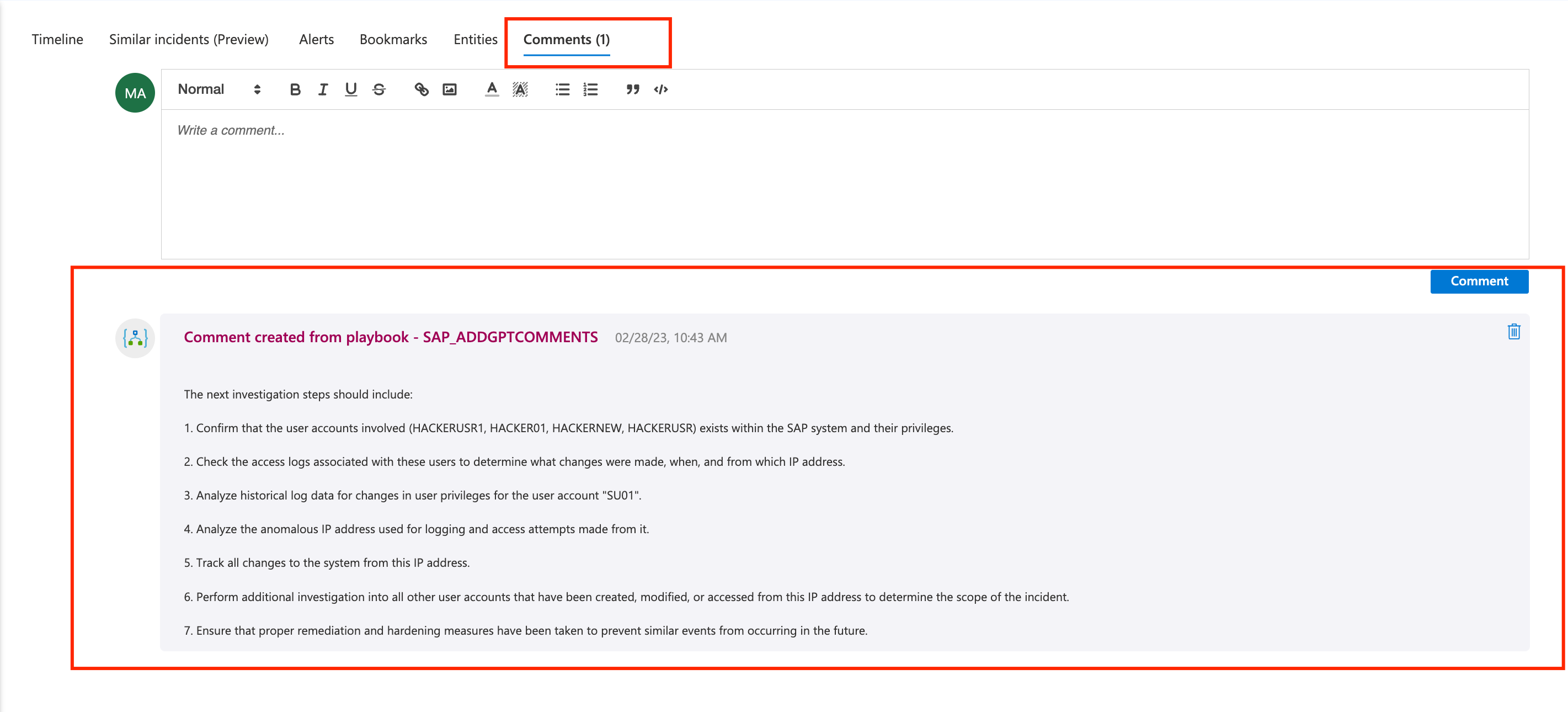
On the incident details page, you can go to Comments tab
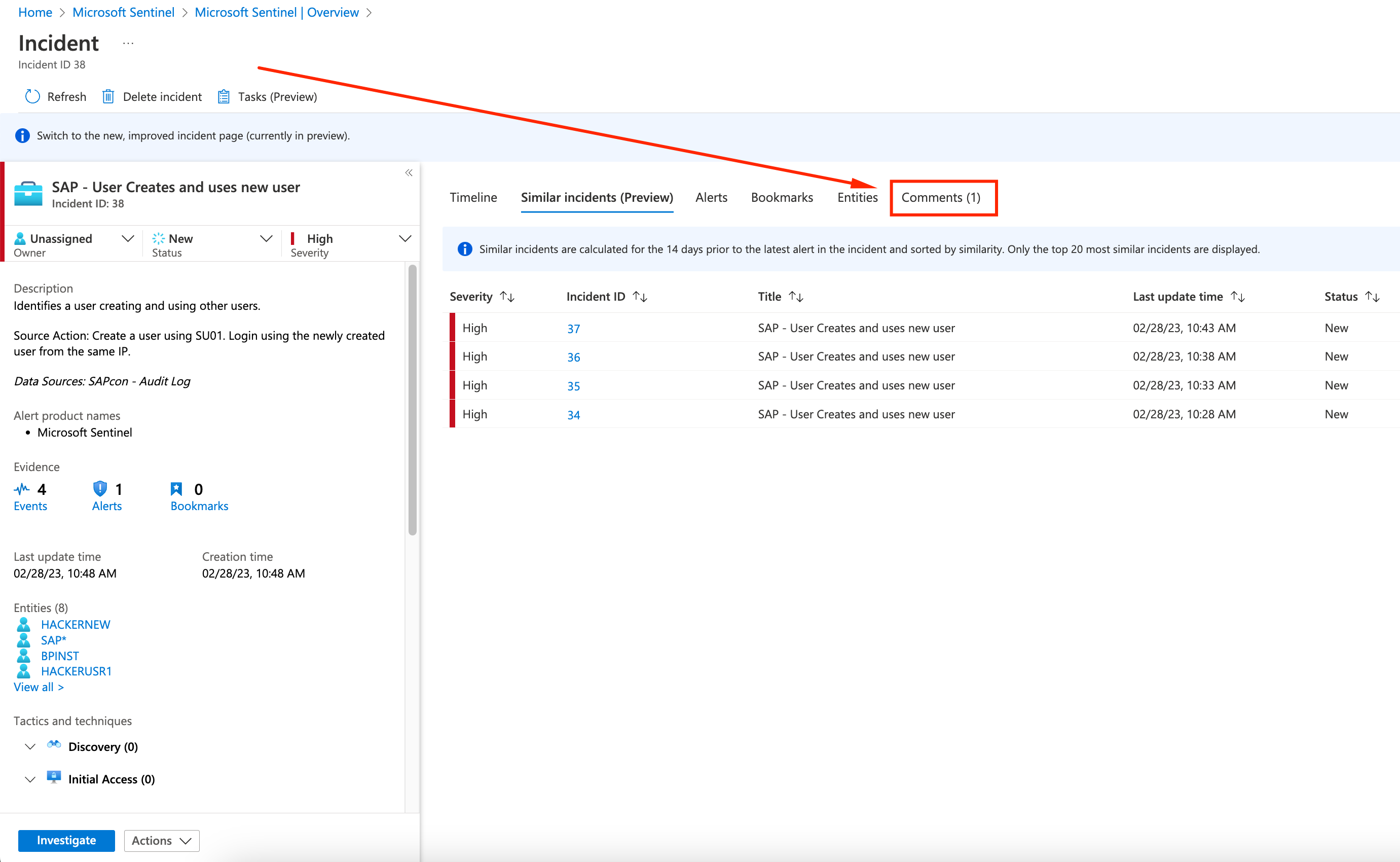
-
If everything worked, you should see a comment added by the playbook with some augmentation regarding the security incident:
Congratulations! In this example we were able to create a playbook, a rule and augment an incident with AI generated information upon a creation of an incident from SAP!